A new threat in the form of Fax messages can infect your PC with ransomware. This Ransomware is distributed via loads of spam emails usually carried out by attackers through intentional spamming campaigns. The subject of these emails is what tricks most users to click it. It could be “Criminal case against you”, inviting most readers to find out what is in the attachment in a state of panic. Eventually, they end up downloading a ransomware downloader.
How Fax messages deliver ransomware
The attachment presuming to carry a fax message “Criminal Case against_You-O00_Canon_DR-C240IUP-4VF.rar”, is actually a password protected RAR archive file that, which when extracted, is a Trojan detected as TrojanDownloader:JS/Crimace.A.
Below is a sample Email message masked as a fax but carrying TrojanDownloader:JS/Crimace.A as an attachment.
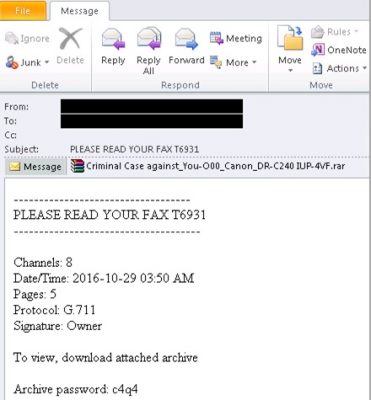
What makes this email message hard to ignore is the fact that it carries all the traits of an authentic fax message. For instance,
- The subject is a simple “PLEASE READ YOUR FAX T6931”
- The message body lists fax protocol, date and time, fax channel and number of pages
- The attachment file name spoofs a popular fax machine brand
- The attached archive file contains a file that has the fake meta-data “—RAW FAX DATA—“
In an attempt to bypass Antivirus scanners, the authors of the ransomware have made use of a password-protected RAR file attachment. The password is provided in the email message body. The archive file contains no fax, but Crimace, a malicious Windows Script File (.WSF) developed in JScript. Crimace then downloads its payload, a ransomware detected as Ransom:Win32/WinPlock.B onto the victim’s PC.
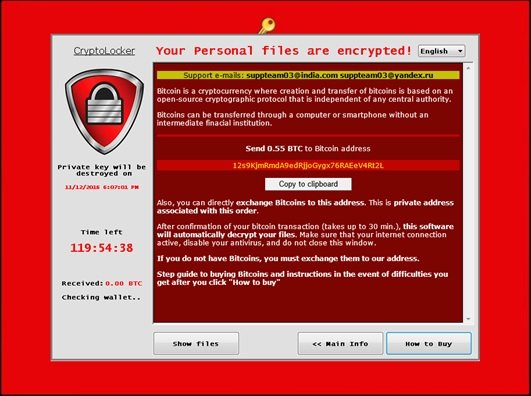
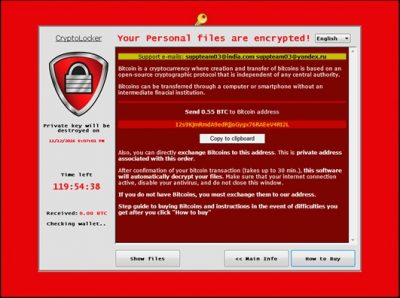
WinPlock ransomware demands 0.55 Bitcoin as ransom
“WinPlock is a family of ransomware that has been around since September 2015 but did not have significant activity until recently. The discovery of this new variant signals that it’s back to wreak havoc. Ransom:Win32/WinPlock.B can search for and encrypt a total of 2,630 file types”, says Microsoft.
WinPlock asks for a ransom of .55 Bitcoin, which the ransom note indicates as US$386 post conversion. Victims have 120 hours to pay the ransom.
Why WinPlock is lethal
When this ransomware family was first detected in Sep 2015, it asked for a ransom of 1 Bitcoin, which at that time converted to ~US$300. However, since then, more ransomware families have flooded the market leading to powerful AV tools to detect them. Hence, with WinPlock coming back with an increase in the ransom amount, there are enough reasons to believe that its authors are looking for greater success and more money.
How to protect yourself from ransomware & stay away from WinPlock
- Use an up-to-date, Antivirus product.
- Keep Windows and the rest of your software up-to-date
- Think before you click. Take a look at the precautions to take when opening email attachments or before clicking on web links.
To read more on WinPlock, click here to read the Technet blog.