CryptoLocker, a deadly ransomware, recently added a new member in its family called as WORM_CRILOCK.A. TrendLabs reports that this new variant is far more dangerous than the known CryptoLocker variants as it carries a notable feature of propagation routines. Further study on this malware brings out the fact that with the addition of propagation routine this can easily spread via removable drives, unlike other known Cryptolocker variants.
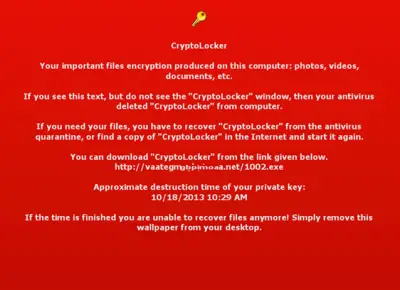
WORM_CRILOCK .A attacks in a totally unexpected manner. Like most CryptoLocker attacks via a downloaded malware, usually UPATRE, WORM_CRILOCK .A acts like an activator for softwares such as Adobe Photoshop and Microsoft Office in P2P file sharing sites. So when malware gets uploaded on P2P sites, cybercrimincals or hackers get easier access to infect the system without even sending any spammed messages and asking users to click.
Speaking on the security threat that WORM_CRILOCK. A possess, Abigail Pichel mentions at the TrendLabs Blog,
“The malware has foregone domain generation algorithm (DGA). Instead, its command-and-control (C&C) servers are hard-coded into the malware. Hard coding the URLs makes it easier to detect and block the related malicious URLs. DGA, on the other hand, may allow cybercriminals to evade detection as it uses a large number of potential domains. This could mean that the malware is still in the process of being refined and improved upon. Thus, we can expect latter variants to have the DGA capability.”
With the threat that this malware could be the new attack weapon of hackers and cybercriminals in the near future, users need to be much more aware of their security measures.
CryptoLockers look for files to encrypt, not just those on your hard drives, but your folders on shared network drives or other connected drives are equally exposed. So, taking a separate backup of your important data should be the first step that you should take. Our blog post, Backup is the best defense against CryptoLocker Ransomware talks in length on the importance of having backups for protecting your data against CryptoLocker attack.
Other important steps should be to use an up to date antivirus program and putting a restriction policy on running executable files on your PC. For complete information on how to protect against Ransomware including CryptoLocker, do refer our detailed blog post on how to prevent Ransomware.
In case you have encountered CryptoLocker, do share your thoughts and experiences.