Security researchers have come across a disturbing trend, which highlights the rise in phishing campaigns targeting WordPress blogs and websites. These campaigns try to lure WordPress site owners by promising free Domain Name System Security Extensions (DNSSEC) upgrade.
New phishing campaign targets WordPress websites
What is Domain name System or DNS, you ask? DNS is a decentralized naming system for resources connected to the Internet. It helps users locate the website’s IP address with a human-friendly rather easy-to-remember name aka URL. For example, www.thewindowsclub.com.
DNS helps web browsers access requested websites without requiring users to enter corresponding IP addresses. However, DNS Spoofing is extremely common these days. In DNS Spoofing, hackers gain control over the DNS database and fill it in with bogus entries, further hijacking web traffic. DNSSEC repels DNS Spoofing.
The DNSSEC essentially protects the existing Domain Name System (DNS) records by adding cryptographic signatures to them, something a website security company Cloudflare also offers.
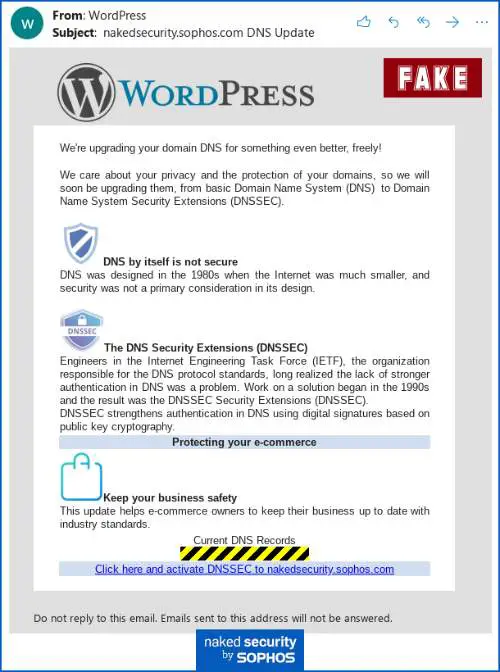
Attackers are trying to trick WordPress blogs and websites owner into taking the bait and giving up the website’s credentials, courtesy of a coordinated phishing campaign. DNSSEC protocol has been around for over 20 years.
“This scam pretended to come from WordPress itself, and claimed that DNS security features would soon be added for our domain,” said researchers.
“It has typically been a feature used by service providers to help to keep their own DNS databases intact when they exchange data with other DNS servers.”
WordPress blogs or websites may fall for this given the enticing promise, which is about providing them with “Secure DNS.” Once you click the link to get your free DNSSEC upgrade, you will be redirected to a web page that claims to be an “Update Assistant.”
This so-called ‘Update Assistant’ then advises the WordPress website owners to enter their WordPress credentials including the username and password. As is the case with nearly all phishing campaigns, it then shows some fake but believable progress messages.
However, this phishing campaign is clearly not limited to WordPress. It also affects Hostgator and Microsoft Azure-hosted websites. Hackers often have access to details about your DNS and hosting providers, which ultimately allows them to reach out to you.
However, always refrain from signing in via links sent in an email. Plus, make sure to turn on Two-factor authentication (2FA) whenever you can. Password managers also help users avoid entering credentials on the wrong websites.