Earlier this year, folks at Microsoft Defender Advanced Threat Protection (ATP) announced the public preview of one of their web protection capabilities in the form of Web Content Filtering. However, this feature was limited to those obtaining a separate license from a cloud-based cybersecurity firm Cyren that used to provide Microsoft Defender ATP customers with a 60-day free trial license. Well, not anymore.
Microsoft makes changes to web content filtering
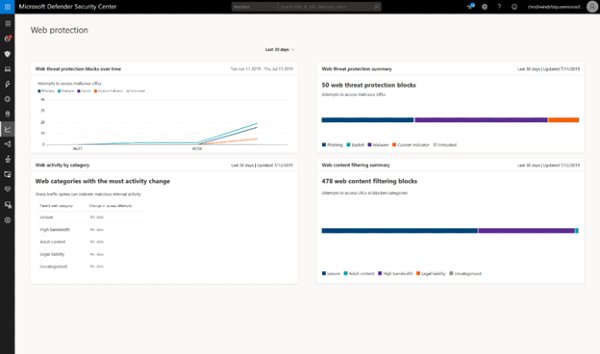
Microsoft has confirmed that web content filtering will now be accessible alongside Microsoft Defender ATP, further eliminating the need for any additional partner licensing. Web content filtering enables organizations to track and regulate access to websites based on their content categories. This filtration applies to websites that are not only malicious but also problematic given the compliance regulations, among other concerns.
In its recent blog post, Microsoft wrote:
“During the public preview, we received positive feedback on the simplicity of the feature due to the ease of creating and deploying policies at scale, without the need for additional agents or hardware. However, one critical piece of feedback we received was that this feature was too expensive to implement, since it required an additional partner license.”
Internal security teams are entitled to policies defined under web content filtering, enabling organizations to track and regulate access to websites based on specified content categories. Organizations can also limit user access to websites and web usage, courtesy of the Microsoft Defender Security Center.
For existing Microsoft Defender ATP customers, their policies will continue to protect their enterprise during or after a 60-day trial for a partner license. Organizations can simply de-authorize the partner licensing integration by navigating to Azure Active Directory > App Registrations, selecting Cyren partner application, and deleting it.
How web content filtering works under Microsoft Defender ATP
Organizations can configure policies within Microsoft Defender Security Center. This way, organizations can easily restrict access to data falling under certain categories. For example, organizations can configure a policy to prevent employees from accessing ‘adult content sites’ across machines. Organizations can also create a separate policy to block ‘high bandwidth sites’ on select machine groups.