Microsoft Defender Advanced Threat Protection (ATP) has announced a new feature that blocks attacks subject to Endpoint detection and response (EDR). The most recent addition to the existing capabilities of Microsoft Defender ATP is known as EDR in block mode. This feature is Microsoft’s attempt to turn EDR detections into blocking and containment of malicious activities.
Microsoft Defender ATP gets EDR in block mode
In its recent blog post, Microsoft had this to say:
“This capability uses Microsoft Defender ATP’s industry-leading visibility and detection capability to provide an additional layer of post-breach blocking of malicious behavior, malware, and other artifacts that your primary antivirus solution might miss.”
The new EDR in block mode capability in Microsoft Defender ATP uses built-in machine learning models to help safeguard Windows 10 users against malicious activities, courtesy of protection engines that excel in threat detection and behavior analysis.
Thanks to this feature, Microsoft Defender ATP can perform real-time threat detection and blocking attacks. These new capabilities should empower business organizations to crack down on several cyberattacks. Organizations can also maintain security posture, further reducing their response time.
EDR in block mode: How does it work?
EDR in block mode immediately stops running processes related to malicious behaviors reported in Microsoft Defender Security Center. Subsequently, security teams within organizations can see details of the threat as well as remediation status. EDR in block mode is already in public preview.
How to turn on EDR in block mode
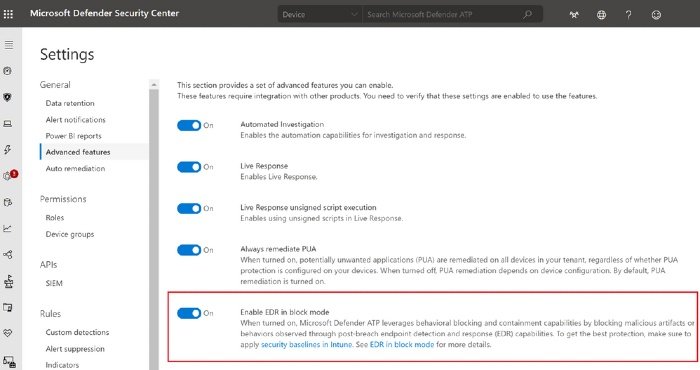
Now that EDR in block mode is in public preview, you can try it now. All you need to do is go to Settings > Advanced features. Switch the toggle for “Enable EDR in block mode” to On. Security teams can also see a similar recommendation in threat and vulnerability management: “Enable EDR in block mode”
Last month, Microsoft Defender ATP announced the public preview of a new risk news feed feature called Event Timeline. It allows IT admins to discover the origin of a particular security threat.
Leave a Reply