Microsoft 365 Defender Research team has released more information about a widespread malware attack injecting malicious ads to Search Engine result pages. The team has notified that this attack has been in work since May 2020 and had reached its peak during August of this year.
Adrozek malware can infect Chrome, Edge, Firefox
During this peak period, around 30,000 devices were getting infected by this issue. Microsoft has also added that popular browsers such as Google Chrome, Microsoft Edge, and Mozilla Firefox are affected by this campaign, indicating that the attacker wants to increase his number of victims.
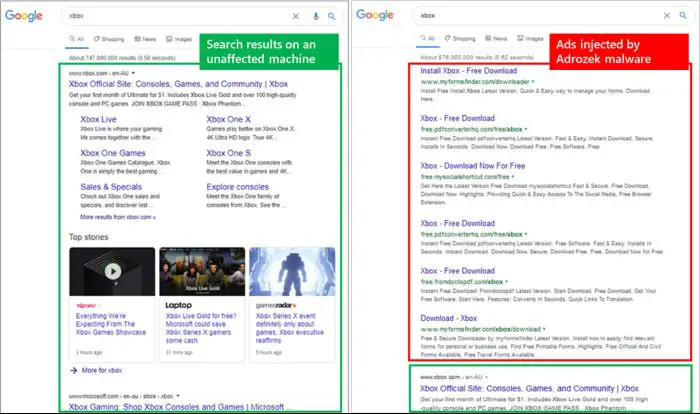
Microsoft has shared a screenshot that compares the search engine result pages of a malware-infected browser compared to one that is not. It was seen that the browser affected by the browser-modifier malware was showing links to third-party websites via affiliate links instead of the actual search engine results.
“We call this family of browser modifiers Adrozek. If not detected and blocked, Adrozek adds browser extensions, modifies a specific DLL per target browser, and changes browser settings to insert additional, unauthorized ads into web pages, often on top of legitimate ads from search engines,” Microsoft said.
The commission paid by the affiliate program is how the attacker earns money, and this kind of attack has been common for an extended period now. Security researchers call this type of malware Adrozek.
While browser-modifier malware campaigns are barely new in the world of digital security, the breadth of this specific malware is beyond comprehension. Since its first capture in May 2020, this Adrozek malware has infected thousands of computers worldwide.
“The intended effect is for users, searching for certain keywords, to inadvertently click on these malware-inserted ads, which lead to affiliated pages. The attackers earn through affiliate advertising programs, which pay by amount of traffic referred to sponsored affiliated pages,” Microsoft added.
As of now, the heaviest points of encounters are situated in South East Asia and Europe. However, considering that the malware can affect almost every popular browser, the volume of encounters would expand further in the upcoming months.
Experts have noted that the motive behind designing malware that works on all browsers is such a huge plan of action. Microsoft Security team has also described the installation and deployment structure of the cryptic malware.
It has used distribution infrastructure to deliver .exe files to users, which releases the primary payload under the disguise of freeware. The payload then manages system-level changes through extensions as well. More importantly, on browsers like Mozilla Firefox, Adrozek goes the additional step to steal critical credentials from users as well.
Leave a Reply