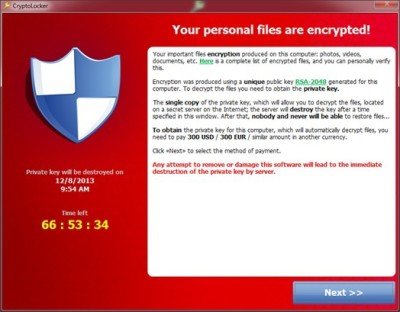
Ransomware Trojan, Cryptolocker was first discovered in September 2013 and are known for attacking PC’s running Microsoft Windows. Cryptolocker could infect PC’s using various sources, the most common being a legitimate email attachment.
Earlier this month, the FBI came out with a status report on Cryptolockers and provided a great relief to the online community. The report claimed that “all or nearly all” of the active computers infected with GameOver Zeus have been liberated from the criminals’ control, and Cryptolocker is “effectively non-functional and unable to encrypt newly infected computers.”
However, according to the security firm Webroot, Cryptolocker ransomware is not dead.
Webroot warned users that Cryptolockers are still very much active and ransomware could be distributed through other botnets, including the likes of CryptoWall, New “CryptoLocker”, DirCrypt and CryptoDefense.
Tyler Moffitt, Threat Team Member at Webroot, said,
“While seizing the majority of the GameOver Zeus Botnets from the suspected “mastermind” Evgeniy Bogachev was a big impact to the number of computers infected with GameOver Zeus – about a 31 percent decrease, it’s a very bold claim to state that Cryptolocker has been “neutralized. The reason why this claim should be scrutinized is because it is only the samples dropped on victims computers that communicated to those specific servers seized that are no longer a threat”.
Tyler further pointed out that most attackers spread their samples through botnets that they either accumulated themselves (Evgeniy), or just rent time on a botnet from someone like Evgeniy (most common). So now after Evgeniy’s servers are seized, malware authors would target other available botnets to spread the ransomware.
Though the FBI has claimed the Cryptolocker to be dead, it would be wise to believe the Webroot’s report and be cautious. As Tyler says, the best way to stay protected is to utilize backups to either the cloud or offline external storage.
Leave a Reply