The recent tests on Linux security solutions by AV-Test Lab indicate a worrisome situation – Linux systems are vulnerable to cyber attacks. Yes, Linux machines are no more completely secure. The test results show that Linux systems can act as a repository of infected files when infected by a malware, waiting for the opportunity to be transferred to connected Windows systems via networking. Such Windows system cannot remain immune to the infection despite the security solutions.
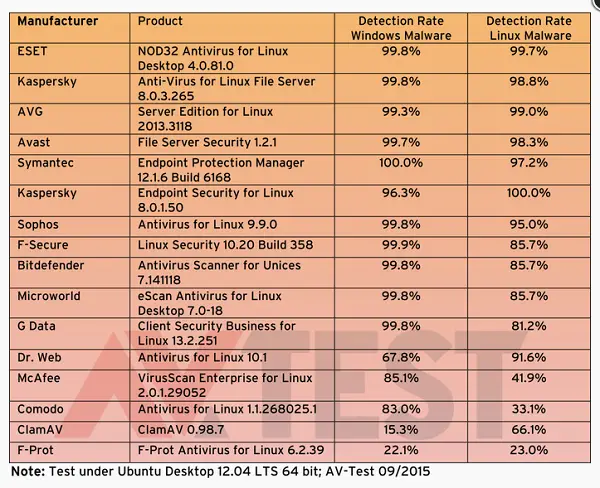
Vulnerabilities in Linux antivirus products
A successful attack normally does not infect the system or the kernel. Rather, it focuses on the applications running on the Linux PC or Web server. They can be more easily hijacked or harnessed as a means to replicate. Major hacker attacks have already been carried out on Web servers via SQL injection or cross-site scripting. But desktop PCs with Linux are also an attractive target. After all, running applications with security gaps are found there as well, e.g. the Firefox browser or tools such as the Adobe Reader.
To do so, it is often sufficient to copy files from a Linux environment to Windows.” it further adds. The most obvious mode of attack involves luring victims to install software or updates via third-party package sources. The team conducted test by running 16 different Anti-virus solutions and splitting test session into three distinct phases,
- The detection of Windows malware
- The detection of Linux malware and
- The test for false positives.
Out of 16 antivirus solutions 8 detected between 95-99% of the 12,000 Windows threat used in the test: The Anti-virus solutions that helped in detection include Bitdefender, ESET, Avast, F-Secure, eScan, G Data, Sophos and Kaspersky Lab (server version).
For more information, visit av-test.org.
Good thing on Linux more apps is open source.
So, linux computers continue function unaffected. The viruses in question are WINDOWS viruses, just stored in the linux computer because of buggy third-party ported software like Flash,Windows Browsers ported to linux, with all their access vices, etc…