Virus Total, the free Internet security service from Google has now been equipped with a feature that lets a user know whether the firmware is infected. We all know, just as any application, even firmware is prone to attacks by different variants of malware, and can also be targeted for surveillance purposes as seen in case of Edward Snowden leaks.
It has been observed that antivirus software usually doesn’t scan the BIOS of a computer. As such, this layer remains unattended and hence, susceptible to attack and cases of breach. Since the BIOS boots a computer and helps load the operating system, by infecting it attackers can deploy malware that survives reboots and wipes system, and since most antiviruses are incapable of scanning this layer, the security can be compromised.
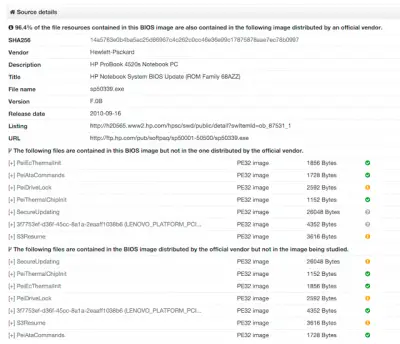
VirusTotal will report firmware malware
With New Virus Total users can take advantage of extraction of the UEFI Portable Executables that make up the image, which represents the code usually used for infection. These executables can then be extracted and submitted individually, allowing users to view a report for each one of them.
Apart from this, users can view details on the firmware they have submitted for scanning by clicking on the Additional information tab where a new Source Details field resides. Also, the File Detail tab will provide important details on the characteristics of the submitted firmware image.
New VirusTotal supports the following tools:
- Apple Mac BIOS detection and reporting
- NVAR variable names enumeration
- ACPI tables tags extraction.
- Strings-based brand heuristic detection
- PCI class code enumeration, allowing device class identification.
- SMBIOS characteristics reporting and more.
It becomes important to mention here that users must remove any private information from BIOS dumps before uploading them to VirusTotal, especially since vendors might store details such as WiFi passwords in BIOS variables.
Leave a Reply