A recently found PUP or Potentially Unwanted Program which is called as DNS Unlocker is causing a major threat to the DNS servers of the PCs. This particular threat of DNS Unlocker was initially considered as a DNS hijack that set the victim’s computer to use specific DNS servers. This looks like a minor issue and it is also simple to fix. However, this is where DNS Unlocker becomes threatening.
What damage can DNS Unlocker cause
According to the WeLiveSecurity blog, the DNS Unlocker PUA possibly does following activities that make it potentially harmful.
- It can set static DNS entries so that the Primary and Secondary DNS servers do not show up in the expected area in the GUI.
- The settings might say that the users are using DHCP, as it is expected when in reality the user is not using DHCP.
The author further describes how this PUA can change settings and take over the victim’s DNS server.
“DNS Unlocker will change a victim’s network settings to use rogue DNS servers. When the victims’ browsers look for google-analytics.com the rogue DNS server will point to a malicious server injecting additional JavaScript. This is done so that advertisements by DNS Unlocker are inserted into web pages using Google Analytics.”
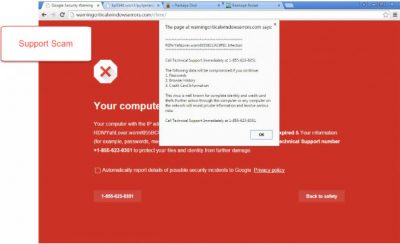
When the DNS Unocker is successful in hijacking the DNS, the user will see advertisements with a note at the bottom saying, “Ads by DNSUnlocker”. The user may also see multiple different variations of “support scam” pop-ups. These screens look as follows:
On the final note, the author mentions why the PUAs are getting a chance to mess up with DNS server of the system.
“Windows will read and use a space-delimited list of DNS server addresses in the NameServer value for an interface, instead of strictly enforcing comma separated lists, PUAs can use this method to hide their DNS settings on your system. This method of hiding rogue DNS settings has been seen in the wild since December 2015, in DNS Unlocker on Windows XP, Vista, 7, 8/8.1 and 10 (x86 and x64).”
You can read the complete report on the DNS Unlocker on the We Live Security blog.
Leave a Reply