The number of malicious programs and malware is constantly on a rise. Furthermore, the apps that are designed to be installed with other programs have also been one of the most preferred ways for virus makers to deploy their payload. In fact, the whole thing is so organized that the affiliate programs help cyber criminals profit off with software downloads. Here is how the Ticno Trojan works the affiliate program bundles the virus with another program which usually ranks high on trustworthiness.
Ticno Trojan
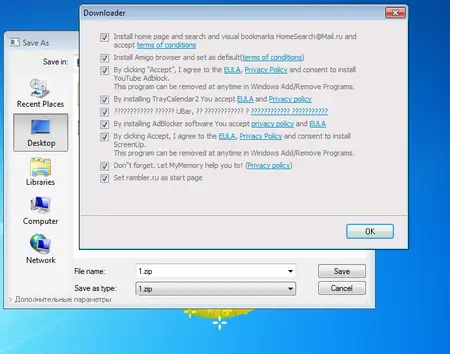
Dr. Web specialists have examined one such downloader Trojan named Trojan.Ticno.1537. The trojan is downloaded by another malware program, After launching the Trojan searches for the virtual environment and starts debugging tools by checking out the names of the processes and the related branches of the Windows system registry. The Trojan.Ticno.1537 verifies the product ID and the computer names. Then the Trojan confirms whether or not perl.exe or python .exe is running.
Once the Trojan is not successful in finding anything suspicious it saves the file named “1.zip” on the disk. By clicking on the “Additional Settings” on the bottom left a corner of the non-standard Microsoft Windows dialog box one can see the list of programs that is ready to be installed on the computer. The screenshot above shows the same in great detail.
In case the user clicks “Save”, Trojan.Ticno.1527 the trojan downloads and automatically installs all of the programs. The Trojan also installs Amigo and [email protected] along with other trojans-including victim’s computer are the browser Amigo and the program [email protected] (developed by Mail.Ru) along with Trojan.ChromePatch.1, Trojan.Ticno.1548, Trojan.BPlug.1590, Trojan.Triosir.718, Trojan.Clickmein.1, and Adware.Plugin.1400. The Trojan ChromePatch 1 is an adware that is usually distributed via the TrayCalender and it is worth mentioning that all the other Trojans are packed in a single installation file.
The worst part, however, is that the Trojan.ChromePatch.1 infects the Chrome resource file-resources.pak and this method is used by Cybercriminals to force display advertisement despite the Trojan being removed from the computer. That being said the size of the Trojan remains unchanged as it searches for strings that contain comment and replace it with its code.
Leave a Reply