In today’s highly advanced digital world, security against data stealing and threats have taken the center stage. One of the major security threats for the organizations could be employees within the organization. Though the most trusted stakeholders of any company; employees can also become the most hazardous security threat. However, if the user privileges are restricted and controlled properly, it can mitigate 94% critical vulnerabilities, says Avecto report 2016. According to Avecto report, removing user privileges can curtail the security threats and data stealing to the maximum level.
What does Avecto report say about removing user privileges
As the report says,
“Analysis of Microsoft “Patch Tuesday” Security Bulletins from 2016 reveals that 94% of Critical Microsoft vulnerabilities would be mitigated by removing admin rights across an organization, up on last year’s figure of 85%.”
The report further says,
“There were 530 vulnerabilities recorded in total, up slightly on the 524 last year, but representing an increase of over 60% since 2013. Despite being Microsoft’s newest and ‘most secure’ operating system to date, Windows 10 was found to have the highest proportion of vulnerabilities of any OS (395), 46% more than Windows 8 and Windows 8.1 (265 each).”
For creating this report, Avecto used the methodology in which vulnerability of the Windows PCs was mitigated by removing user privilege.
94% vulnerabilities can be mitigated by removing Administrator rights
Some of the key findings of the Avecto report are as follows:
- Of the 189 vulnerabilities in 2016 with a Critical rating, 94% were concluded to be mitigated by removing administrator rights
- 66% of all Microsoft vulnerabilities reported in 2016 could be mitigated by removing admin rights
- There has been a 62% rise in the total volume of vulnerabilities since 2013
- 100% of vulnerabilities impacting Microsoft’s latest browser Edge could be mitigated
- 100% of vulnerabilities in Internet Explorer could be mitigated by removing admin rights
- 99% of vulnerabilities affecting Microsoft Office could be mitigated by removing admin rights
The Avecto report has further categorized the Microsoft vulnerabilities in 2016. These include Remote code execution, Information disclosure, elevation of privilege, denial of service, security feature bypass, spoofing, and tampering. A detailed graph showing how these vulnerabilities were mitigated by removal of admin rights is also generated by the Avecto report. This graph looks as follows:
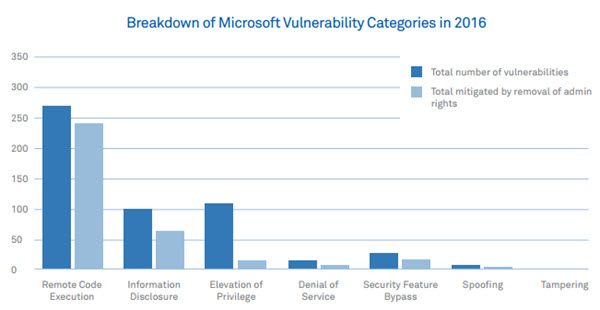
The Avecto report on vulnerability mitigation by removal of admin rights is certainly a great finding that will help organizations to secure their data. You can download this report from Avecto website.
Is turning UAC up to highest any protection (?)
Basically use a Standard User account for your day to day computing work. Turning UAC to the highest Always Notify Me will harden security – but keeping the UAC at default is fine too.