Most malware and viruses have evolved with time and use disguise to conceal their identity. Even the most active CERBER family of ransomware has adopted a new technique to evade detection by machine learning solutions.
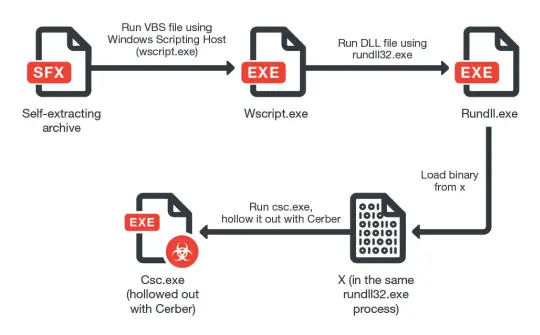
This development was first observed by researchers at Trend Micro Inc. They reported that the new version of the Ransomware uses a new loader designed to bypass detection by Machine Learning solutions by separating the different stages of the malware into multiple files and then dynamically injecting them into running processes.
The problem with self-extracting archives, such as WinRAR, is that they hide the fundamental content of the file. So machine learning, with all that information hidden from it, is more likely to give inappropriate answers”, says Jonathan Oliver, Trend Micro.
Cerber Ransomware evolves
The latest version of Cerber also differs from its earlier iterations in a way that although the mode of attack is same i.e., delivered via malicious phishing email, the emails contain a link to Dropbox that downloads and self-extracts the malware payload itself. The following flow chart can help you understand the concept better.
Once installed, the malware version runs an identity check to verify if it is running on a virtual machine or sandbox. If anyone of it is detected, the malware immediately stops running to avoid the Cerber code being detected and analyzed. It has been found that cyber security researchers normally follow this modus operandi to analyze malware and stop it from spreading throughout the network.
Trend Micro Inc acknowledges, new and emerging threats will always try to get around the latest solutions. As such, users should avoid relying on any single approach to security. A proactive, multilayered approach to security can prove to be more effective. Smart Protection suites and other security tools can protect users and businesses from these threats by detecting malicious files, and spammed messages as well as blocking all related malicious URLs.
For more information, see this TrendLabs Security Page.
Leave a Reply