Instances of the use of malware-laced PowerPoint files that infect your PCs with malware are well known but the recent ongoing spam campaign highlights a worrying trend. A simple PowerPoint trick makes it possible to drop malware without even requiring a user to click a link.
The finding was made by TrendMicro, one of the best global leaders in antivirus cloud computing security and internet content security software for PC& Mobile.
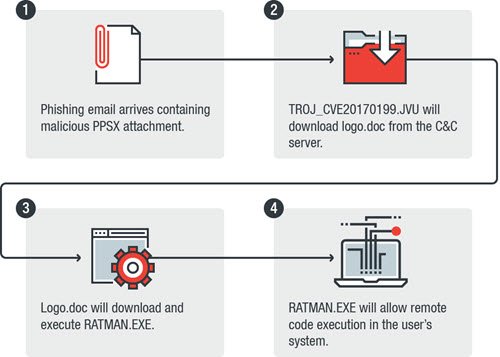
We recently observed a new sample (Detected by Trend Micro as TROJ_CVE20170199.JVU) exploiting CVE-2017-0199 using a new method that abuses PowerPoint Slide Show—the first time we have seen this approach used in the wild before. As this is not the first time that CVE-2017-0199 was exploited for an attack, we thought it fitting to analyze this new attack method to provide some insight into how this vulnerability can be abused by other campaigns in the future, reported the website in a blog post.
The malware is a banking Trojan designed to get remote access to an unknown user, network traffic monitoring and other nefarious capabilities. It is mainly delivered to users via a spam email with a PowerPoint Show (PPS). These files differ from usual PowerPoint files (PPT and PPTX) in a way that they cannot be edited. Moreover, they can only be opened in slideshow or presentation modes.
Malicious links that are carefully embedded in the PowerPoint slides install the trojan as soon as they sense any hovering or a mouse-over action. For users, having the latest version of Office software installed and Protected View enabled, the malware uses a security prompt to execute the malicious code. As such, users should resist from clicking “Enable” button in such dialog boxes, unless completely aware of the consequences.
In addition to implementing effective mitigation techniques, all PowerPoint users should employ a multilayered solution to get a comprehensive defense against targeted attacks and advanced threats, says TrendMicro.
Leave a Reply