A vulnerability has been detected in Microsoft Outlook that risks users credentials being hacked by attackers. Discovered by Will Dormann of the CERT Coordination Center (CERT/CC), the vulnerability allows hackers to steal user’s Windows password just by having the target preview an email with a Rich Text Format (RTF) attachment that contained a remotely hosted OLE object.
The bug has already been patched by Microsoft as part of its April Patch, almost a year after it was first identified.
The Microsoft Outlook flaw
Explaining the vulnerability Dormann wrote,
Outlook blocks remote web content due to the privacy risk of web bugs. But with a rich text email, the OLE object is loaded with no user interaction. Let’s look at the traffic in Wireshark to see what exactly is being leaked as the result of this automatic remote object loading.
Here we can see than an SMB connection is being automatically negotiated. The only action that triggers this negotiation is Outlook previewing an email that is sent to it.
The Microsoft Outlook vulnerability can leak even Windows login credentials letting attackers take full control over the PC. As Microsoft Outlook automatically renders OLE content, it will initiate an automatic authentication with the attacker’s controlled remote server over SMB protocol using single sign-on (SSO), handing over the victim’s username and NTLMv2 hashed version of the password, potentially allowing the attacker to gain access to the victim’s system.
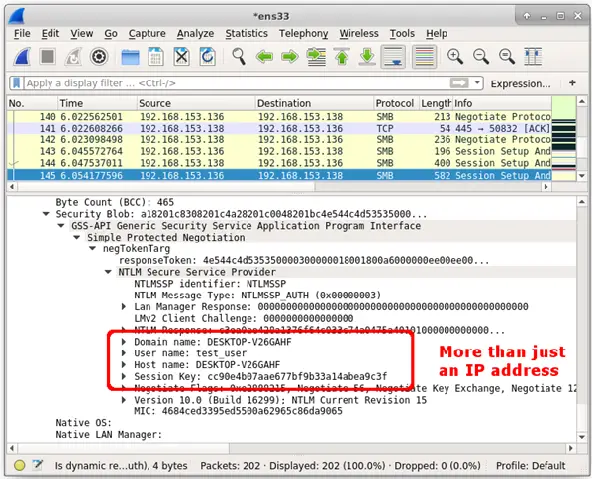
This may lead to the following credentials getting leaked (refer above screenshot),
- IP address
- Domain name
- User name
- Host name
- SMB session key
Impact of the OLE Web Bug
This bug can hit victims in following two ways,
Windows crash
As Outlook can be compromised to initiate an SMB connection to an arbitrary host. Upon connecting to a malicious SMB server, Windows may crash. An example of this incident can be explained as below,
- A rich text email in Outlook is made to point to an SMB server that exploits this vulnerability
- Once Outlook previews such an email message, Windows will crash with a Blue Screen of Death (BSOD)
- Every time Outlook is launched after encountering such a scenario, Windows will BSOD crash again because Outlook remembers the last email message that was open
Collecting Password hashes
As per Dormann’s research, the vulnerability is capable of leaking more than just the IP address of the victim.
Any passwords that are words (like “test”) or patterns (like “asdf”) are much easier to crack than randomly-generated passwords, since most cracking tools have rules to check for such things. Moreover, the hackers may have access to high-end GPUs, allowing them to crack common passwords with ease.
Microsoft issues half-hearted fix
Although Microsoft issued a much-delayed fix that prevents Outlook from automatically initiating SMB connections when an RTF email is previewed, Dormann says that it is not a complete full proof solution. He mentions,
“It is important to realize that even with this patch, a user is still a single click away from falling victim to the types of attacks described above. For example, if an email message has a UNC-style link that begins with “\\”, clicking the link initiates an SMB connection to the specified server.
How to avoid this vulnerability
- Install Microsoft update CVE-2018-0950 if you haven’t
- Block inbound and outbound SMB connections at your network border.
- Block NTLM Single Sign-on (SSO) authentication, as specified in Microsoft Security Advisory ADV170014.
- Ensure that your Windows login has a sufficiently complex password so that it is resistant to cracking. For better passwords you may do the following,
- Use a password manager to help generate complex random passwords.
- Use longer passphrases (with mixed-case letters, numbers and symbols) instead of passwords.
Stay safe!
Leave a Reply