The Coronavirus malware that recently started infecting computers by luring the consumers about information about the new preventive measures for coronavirus-related pneumonia has a solution. This malware delivered the Emotet payload.
The official antidote comes from JPCERT Coordination Center, which maintains the JPCERT/CC’s official repositories. They have developed this using Microsoft Visual Studio Community on Windows 10. The tool Checks for Emotet malware infection, and reports its exact location.
EmoCheck Emotet malware detection tool released
The solution comes with the name of the EmoCheck tool, which checks for Emotet malware infection on the computer. Emotet is known to generate its process name from a specific word dictionary and C drive serial. EmoCheck Tool scans the running process on the host, and find Emotet process from their process name.
Using this tool is simple. Download the version (32 or 64 bit) from here and double click to run the scanner. Once done, you should get a similar message as below if the computer is infected with the virus.
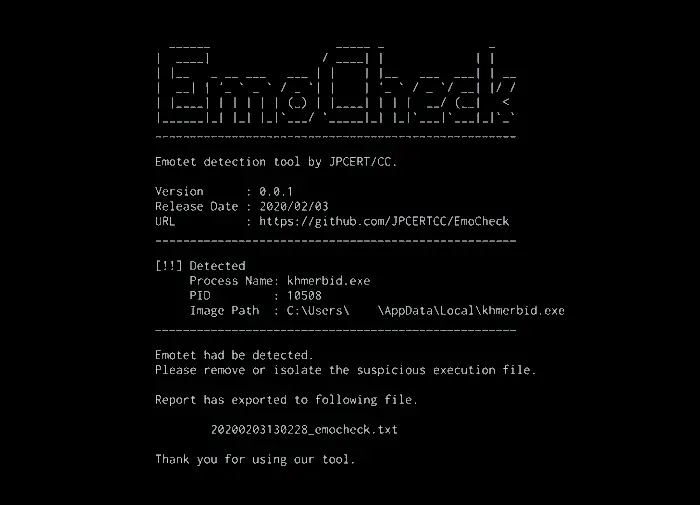
Sample Report of EmoCheck Tool Scan
Emocheck v0.0.1]
Scan time: 2020-02-03 13:06:20
____________________________________________________
[Result]
Detected Emotet process.
[Emotet Process]
Process Name : khmerbid.exe
Process ID : 10508
Image Path : C:\Users\[username]\AppData\Local\khmerbid.exe
____________________________________________________
Please remove or isolate the suspicious execution file.The report will be exported to the following path:
[path of emocheck.exe]\yyyymmddhhmmss_emocheck.txt
Once you open the report, you will have the exact filename of the malware. We suggest booting your computer into safe mode without network, and then delete the file.
That said, while you can remove the virus from the computer, remember that there is a second module that is part of the payload. The module can steal user credentials, sensitive documents, browser history, and more. In my view, it would be best to reset your computer to stay safe.
Since Japan was hit with this malware, the developers have tested it on Windows 10 1809 64-bit Japanese Edition, Windows 8.1 64-bit Japanese Edition, Windows 7 SP1 32-bit Japanese Edition, and Windows 7 SP1 64-bit Japanese Edition. Technically it should work on all Windows 10 versions.
Once you are through, make sure to enable Tamper Protection in Microsoft Security, and in the future, never open an email that asks you to enable content to view what’s inside the document.