If you are an Enterprise or Small Business using Microsoft’s Threat & Vulnerability Management service, then some good news for you all. Microsoft has announced support for Tamper Protection. It’s a brilliant feature which comes as part of Windows Security, Microsoft’s inhouse Security and antivirus solution for Windows. While it is available for consumers, getting to the Enterprise is a piece of great news.
Do note that Microsoft did announce Tamper Protection available for all Microsoft Defender ATP customers. Still, it was not available for Microsoft Defender ATP Threat & Vulnerability, and earlier versions of Windows.
Tamper protection is now available for Enterprise
Tamper Protection feature prevents malicious apps from changing important Windows Defender Antivirus settings. It includes real-time protection, controlled folder access, cloud-delivered protection, and so on. Enterprise who are completely dependent on Microsoft Defender ATP or the Microsoft Threat Protection solutions would never want an end-user or software to change those settings.
How to enable using TVM service (Threat & Vulnerability Management)
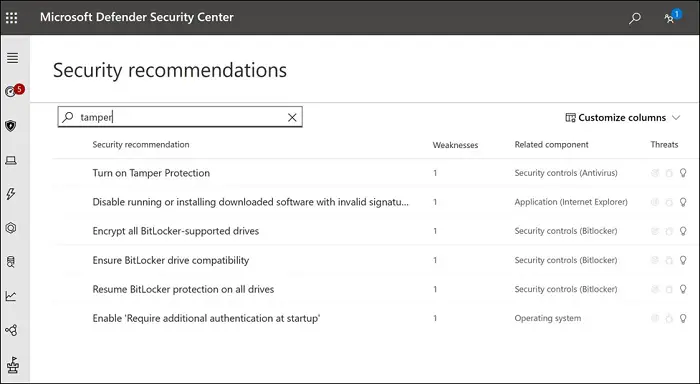
To check the status of tamper protection, IT admin can go to the Security recommendations section, and search for the keyword “tamper.” The result should reveal a setting, “Turn on tamper protection.” When you open it, it reveals a list fo exposed machines. You can export the exposed device list, and enable the feature on those devices. The screen also offers you the ability to monitor changes over time, and a process to turn on the feature.
Enable Tamper Protection on previous Windows 10 versions
Noe every organization is on the latest version of Windows, and Security should not be a criterion for it. Keeping this mind, Microsoft has enabled this feature for earlier versions of Windows. Microsoft recommends enabling this feature using Intune based on user or device groups. It is applicable for customers with Windows versions 1709, 1803, and 1903.
To enable, go to Microsoft Endpoint Manager > Device Configuration – Profiles > Create profile > Endpoint protection and configure tamper protection. To confirm, you will have to use the Get-MpComputerStatus PowerShell cmdlet, and check if the value of IsTamperProtected is set to A.
There are more ways to enable Tamper Protection. It includes the registry method. Follow our guide to learn more about it.
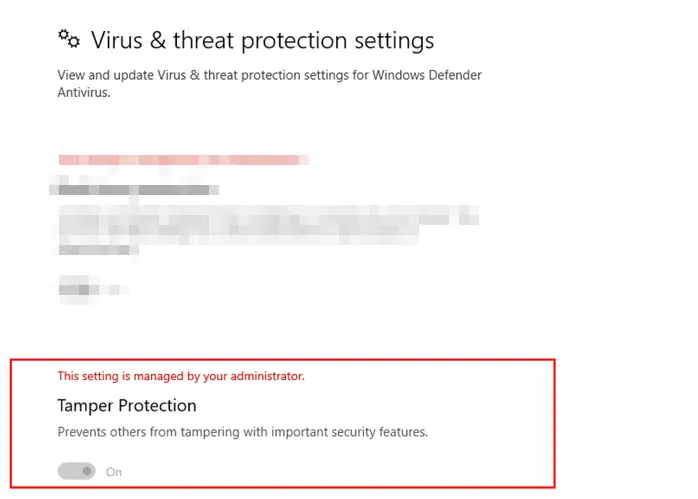
Once enabled, the end-users in the Enterprise will not be able to change it. When they open the Windows Security app, they should see a message—This setting is managed by your administrator.
Leave a Reply