Wi-Fi users, beware! Security researchers have discovered a major security vulnerability, which allows nearby attackers to spy on your encrypted Wi-Fi traffic. Formally known as CVE-2019-15126, the vulnerability also goes by a different name – Kr00k. Cybersecurity firm ESET has released a new whitepaper explaining how Kr00k can slip deep inside your Wi-Fi encryption and pose numerous privacy risks.
If exploited on a large scale, the Kr00k vulnerability puts at risk more than a billion computers, smartphones, and other modern devices that can connect to Wi-Fi. A previously unknown vulnerability is essentially a design flaw present in Wi-Fi chips.
Devices containing Wi-Fi chips by Cypress and Broadcom remain susceptible to the Kr00k vulnerability. These Wi-Fi chips are highly common and they power more than a billion Wi-Fi-capable devices like computers, smartphones, tablets, and IoT products.
The list of popular devices affected by Kr00k
- Amazon Echo 2nd gen
- Amazon Kindle 8th gen
- Apple iPad mini 2
- Apple iPhone 6, 6S, 8, XR
- Apple MacBook Air Retina 13-inch 2018
- Google Nexus 5
- Google Nexus 6
- Google Nexus 6S
- Raspberry Pi 3
- Samsung Galaxy S4 GT-I9505
- Samsung Galaxy S8
- Xiaomi Redmi 3S
In addition to client devices, the CVE-2019-15126 also puts at risk Wi-Fi access points and routers with Broadcom chips. If exploited, the vulnerability allows bad actors to decrypt certain wireless network packets transmitted by a vulnerable device.
For this to work, an attacker looking to spy on your encrypted traffic has to be physically near you. If the person is successful in exploiting the vulnerability, he/she can then snoop on websites you visit, in addition to your sensitive, private information, among others.
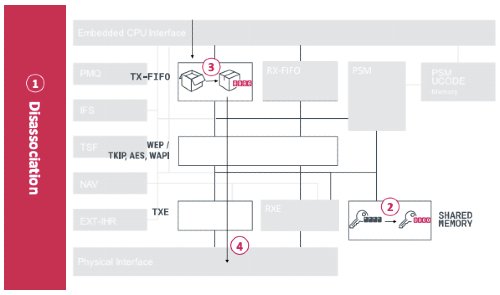
First things first, Kr00k causes vulnerable devices with unpatched chips to use an all-zero key. As part of the dissociation process, it encrypts a part of the target user’s communication using an all-zero key. This leads to an attacker causing dissociations to capture and decrypt private user data.
“After a dissociation occurs, data from the chip’s Tx buffer will be transmitted encrypted with the all-zero TK. These data frames can be captured by an adversary and subsequently decrypted. This data can contain several kilobytes of potentially sensitive information, says ESET.
“This is possible even if the attacker is not connected (authenticated and associated) to the WLAN (e.g. doesn’t know the PSK) – by using a WNIC in monitor mode – which is what would make Kr00k advantageous for the attackers, compared to some other attack techniques used against Wi-Fi security.”
Researchers also examined devices with Wi-Fi chips from other manufacturers like Qualcomm, Realtek, Ralink, Mediatek for Kr00k vulnerability. However, they not see the vulnerability manifest itself in those devices.
Leave a Reply