Researchers at Vullnerability have identified more than 670 subdomains that had previously been used by Microsoft. Researchers warn that attackers could easily hijack hundreds of subdomains that Microsoft has long been forgotten about.
In shocking revelations, hundreds of now-defunct Microsoft subdomains have been found vulnerable to phishing, malware, and many other malicious activities. Experts warn that attackers could easily hijack and gain unauthorized access to these subdomains.
Hackers could hijack these Microsoft subdomains for phishing
These Microsoft subdomains carry a significant brand value. As a result, cybercriminals could fool their victims into installing malware and exposing their login credentials and credit card details with the help of Phishing and other social engineering methods.
As discovered by researchers, some of the Microsoft subdomains that could be subject to subdomain takeover attacks are as follows:
- identityhelp.microsoft.com
- mybrowser.microsoft.com
- web.visualstudio.com
- webeditor.visualstudio.com
- data.teams.microsoft.com
- sxt.cdn.skype.com
- download.collaborate.microsoft.com
- incidentgraph.microsoft.com
- admin.recognition.microsoft.com
- api.getdevices.microsoft.com
- dev.social.microsoft.com
- manage.codesign.microsoft.com
Expired hosting services and DNS misconfigurations are responsible for subdomain takeover. Once attackers gain full access to a subdomain, they can upload their own files, create their own databases, track data traffic and also create a clone of the main website.
“It is not possible to detect that the subdomain is hijacked by an attacker and it threatens the security with various attack scenarios.”
As researchers describe, there are some obvious signs of subdomain takeover vulnerability.
In case of a hostile takeover of a subdomain, a website will throw a 404 error code and display messages like “Site not found”, “This site doesn’t exist.” Affected subdomains will mostly be redirected to other malicious websites controlled by an attacker.
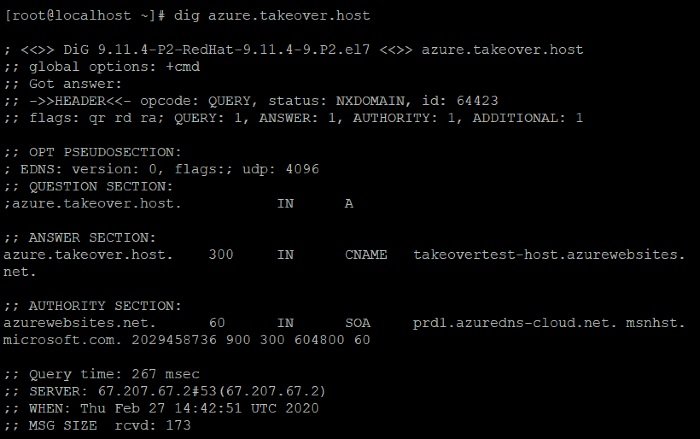
But in some cases, it may not be easy to figure out whether a subdomain is vulnerable or not. In that case, researchers recommend reviewing DNS records. HTTP responses are not available in Microsoft Azure. Researchers show an example of a vulnerable subdomain on Azure.
While reviewing DNS records, it’s highly important to pay attention to STATUS and CNAME. It provides information as to where the subdomain is hosted. In that case, attackers could forge source on the Microsoft Azure portal and takeover the subdomain.
According to researchers, service providers like Github, Amazon Web Services, Azure, Shopify are vulnerable to subdomain takeover attacks.
Leave a Reply