Microsoft has released information about a new class of device, Secured-core PCs, which they have developed working internally with OEM partners such as Lenovo, HP, Dell, Panasonic, Dynabook, and Getac. This new breed of the device makes sure that the consumers don’t have to go through making complex choices to secure their device from Kernel attacks.
Secured-core PCs to offer Chip-to-Cloud security against Kernel attacks
The current scenario involves customers to make changes both to the OS and the BIOS/UEFI settings to make sure hardware-backed security is enabled on the computer. If anything is not set correctly, malware payload can be delivered by existing software or through drivers.
Secured-core PCs, on the other hand, have the hardware-backed security feature enabled by default. The customers need not do anything. Here is the list of hardware-backed security features are enabled by default on any Secured-core PC:
| Security promise | Technical features |
| Protect with hardware root of trust | TPM 2.0 or higher TPM support enabled by default Virtualization-based security (VBS) enabled |
| Defend against firmware attack | Windows Defender System guard enabled |
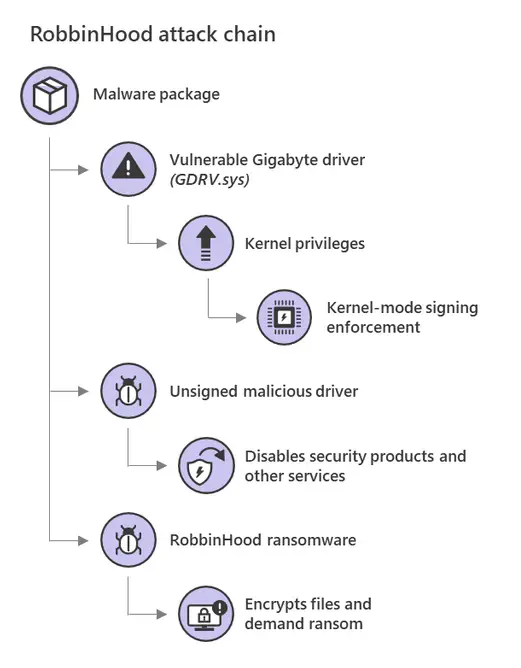
| Defend against vulnerable and malicious drivers | Hypervisor-protected code integrity (HVCI) enabled |
| Defend against unverified code execution | Arbitrary code generation and control flow hijacking protection [CFG, xFG, CET, ACG, CIG, KDP] enabled |
| Defend against limited physical access, data attacks | Kernel DMA protection enabled |
| Protect identities and secrets from external threats | Credential Guard enabled |
These settings will make sure that hardware-backed security features are enabled, and they will make sure that the computer firmware is always safe from vulnerable and malicious drivers and unverified code execution.
Along with this, Microsoft is also enabling a couple of more security features. It includes a combination of Secured-core services, seamlessly integrates with Microsoft Defender ATP, lighting up additional security scenarios, and providing unified protection against the entire attack methodology.
That said, this approach is not new to Microsoft. This feature has already been implemented with Azure Sphere, the integrated security solution for IoT devices and equipment.
How to enable the same settings on your computer?
While this is coming with the new devices, how can the existing consumers make sure to secure their devices the same way? Microsoft recommends enabling Secure boot, HVCI (enables VBS), KDP (automatically turned on when VBS is on), KDMA (Thunderbolt only), and Windows Defender System Guard.
If you are looking to buy a Secured-core PC, there are few available. It includes Lenovo ThinkPad X1 Yoga 4th Generation, Dell Latitude 7400 2-in-1, HP Elite Dragonfly, Microsoft Surface Pro X for Business, Panasonic TOUGHBOOK 55, Dynabook Inc. Portégé X30-F1352 and more. Find the full list on the official website.
Leave a Reply