A critical security vulnerability has been found and fixed in Microsoft Teams, the software giant’s enterprise communication service. This security vulnerability affected Teams’ desktop and browser versions. If exploited, it could severely affect the cybersecurity infrastructure of companies, leading to widespread data theft campaigns, corporate espionage, ransomware attacks, among others.
Account takeover vulnerability in Microsoft Teams
The use of Microsoft Teams and remote communication services, in general, has increased to a significant extent. As more companies have transitioned to the work-from-home arrangement, Microsoft Teams continues to witness a surge in overall consumption. As a result, attackers have turned their focus towards Teams.
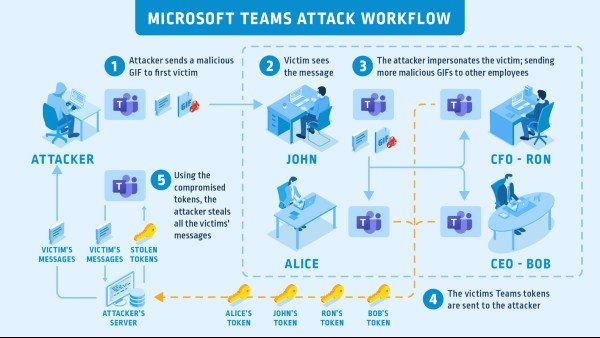
Researchers at a cybersecurity firm CyberArk have identified a critical, account takeover vulnerability in Microsoft Teams that puts sensitive company data like credentials and conversations at risk. If exploited, attackers can scrap all data associated with affected Teams accounts. For this hack to work, hackers use compromised subdomain and a malicious GIF file.
This account takeover vulnerability tends to spread automatically. In its research, CyberArk wrote:
“Imagine the following scenario. An attacker sends a GIF or an image to a victim and gets control over their account. This vulnerability worked just that way and had the potential to take over an organization’s entire roster of Microsoft Teams accounts.”
What goes behind the scenes
This critical, account takeover vulnerability exists in the way Teams passes the authentication access token to image resources. As researchers describe the procedural flow of the hack, the attack starts with a malicious GIF.
Microsoft’s authorization server creates temporary JWT access tokens every time you want to access Teams. Several other Tokens are also created for letting users access other services like SharePoint, Outlook, etc. Access tokens like these also apply to image content. Authentication APIs play a significant role in ensuring authenticated user-communication across services.
Although Teams authenticates the user in front of its API interface. However, the situation is a whole lot different when it comes to images.
“Loading images is a bit more complicated authentication-wise if you don’t base your user authentication method on cookies.”
Teams manages most of the JWT tokens in the browser’s local storage while cookies only play a role in the authentication process. However, loading images is uncertain because the server holding the images first needs to authenticate the right user.
Teams sets an image “src” attribute of a URI to an HTML IMG tag. Microsoft uses a cookie called “authtoken” and “skypetoken_asm” that could present a problem. Researchers observed Teams creates the skype token, which can make APIs calls/actions through Teams API interfaces in association with an authentication token.
“If you can get your hands on this authtoken, you can easily create a skype token – and that’s a really interesting thing for an attacker to take advantage of.”
Microsoft has fixed the vulnerability
In the case of GIF, attackers could use an “src” attribute pointing to the compromised sub-domain via Teams chat. Researchers worked with Microsoft Security Research Center under Coordinated Vulnerability Disclosure after finding the account takeover vulnerability.
The vulnerability was reported to Microsoft on 23/03/20. Microsoft corrected misconfigured DNS records on 23/03/20 and issued a patch on 20/04/20.
Leave a Reply