In the past couple of years, we have seen a range of Ransomware making rounds on the internet. Strangely enough, this also included a Ransomware that faked encrypting files and pulled a bluff. While the intent of most ransomware is to make money, some of them beg to differ. The latest one to do so is a rather cruel spin-off of the horror movie franchise, and it is the Annabelle ransomware.
Annabelle ransomware
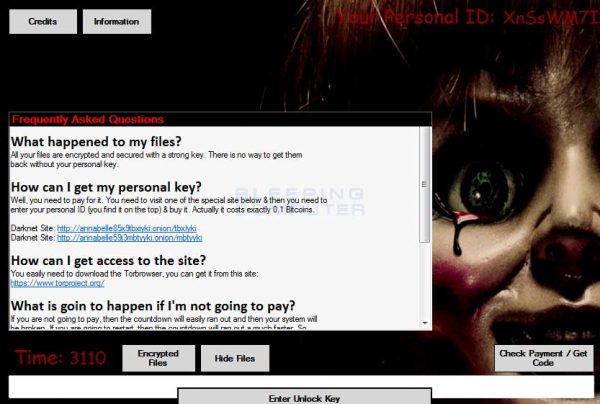
The Ransomware called Annabelle was discovered by security researcher Bart. Annabelle is every bit same as the usual Ransomware, but it is designed to show off the skill of the developer rather than to generate the money. Once installed the Ransomware disables Windows Defender, turns off the firewall, encrypts your files and then tries to spread via USB drives. Meanwhile, the Ransomware overwrites the master boot record of the infected computer and replaces it with a bootloader.
After configuring itself, Annabelle will make sure that it terminates a bunch of programs like Process Hacker, Process Explorer, Msconfig, Task Manager and Chrome. In the next step, the ransomware configures Image File Execution registry so that other programs like Notepad++, Notepad, Internet Explorer and others cannot be opened. However, this method fails miserably on newer versions of Windows that don’t support autoplay feature.
Finally, the Annabelle ransomware will start encrypting the computer with a static key, and all the files will be appended to the .ANNABELLE extension. Now the system will reboot, and then the user will see the lock screen as shown above. The developer assumes a pseudo-name of iCoreXo812 and details a way to contact him on Discord. Moreover just to exhibit his/her skills, the developer has mentioned himself on props screen and the master boot record of the infected computer. On the brighter side since Annabelle Ransomware uses Stupid Ransomware and this can be decrypted by using Stupid Decryptor.
You can read more about this on bleepingcomputer.com.
thank you