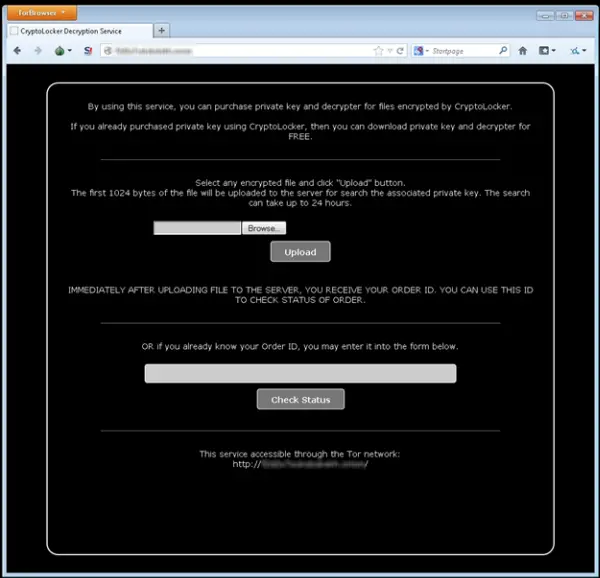
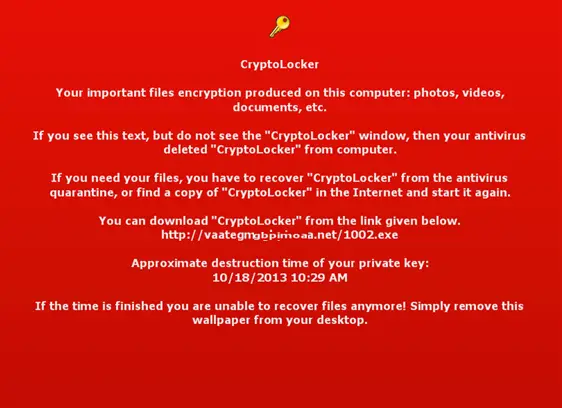
The incidence of Cryptolocker ransomware is on the rise. Commonly named as Crilock, this malware strain is affecting the Windows computer systems widely – especially in Europe. This ransomware enters your computer network and encrypts your files using public-key encryption, and unlike other malware this encryption key remains on the hacker’s server.
Infected users are asked to pay amounts in the range of $300 as a ransom to receive this private key. The users are also threatened that if the ransom is not paid in three days, the key will be destroyed, and you may lose your files forever. You can get the private keys once you pay the ransom which can be paid using various online payment modes like Ukash, Paysafecard, MoneyPak, CashU and BitCoin. However, it is never recommended paying the ransom as it may encourage such activities.
According to the warnings coming from UK’s National Crime Agency this Trojan has been targeting English-speaking countries predominantly. Cryptolocker comes via email in the form of some email attachments of PDF attachment from some banks or some kind of financial institutions. Downloading some other malware may also bring Crilock to your system. Zbot from Upatre is one of the most commonly spammed malware which downloads Crilock to your computer system.
Once downloaded the ransomware starts encrypting the local files saved in your computer system and demands a ransom of two BitCoins in exchange of the private key to decrypt the files. CryptoLocker targets the files with extensions .doc, .docx, .xlk, .xls, .xlsb, .xlsm, .xlsx and much more. The decrypt key is unique for each encrypted file.
Taking the back-up of all your sensitive and important files is the best defense against this exasperating ransomware Cryptolocker because you won’t be able to decrypt the encrypted files once the Trojan hit your computer system even if you manage to remove the malware.
If the System Restore Point is turned ON in your computer system before getting infected with Crilock you can recover the previous versions of encrypted files. You can recover the files stored in your computer system and not the ones stored in some removable drive.
Backup Backup Backup
Says Microsoft:
Crilock is not the first malware to extort money by encrypting files and it certainly won’t be the last. However, you can help prevent Crilock and other malware, from infecting your PC by:
- Keeping your operating system and antivirus product up-to-date.
- Being careful about which files you download.
- Being cautious about which attachments and links you open.
Ransomware such as Crilock also emphasizes the importance of backing up your files on a regular basis. You can back up files by enabling System Restore, using manual syncing methods, or even by manually moving your files to a separate drive.
In some cases, you can recover previous versions of encrypted files. However, the following conditions must be in place:
- System Restore Point must have been turned on before you were infected with Crilock.
- You must already have detected and removed Crilock, and there can be no traces of it on your PC.
- Your files must be on the same PC you’re using to recover them (that is, the files aren’t on a network or removable drive).
SkyDrive for Windows 8.1 also has a means of restoring previous versions of Microsoft documents. Similar to System Restore Point, you can look at the version history and recover files from a previous state.
Surveys from various security companies found that more than 10,000 Cryptolocker victims are reported predominantly in the US & Europe from October 27- November 1, 2013.
HitmanPro.Alert is a free Ransomware Protection & Browser Intrusion Detection Tool. CryptoPrevent is another handy tool which provides your computer a shield against Cryptolocker or any other kind of ransomware. Anvi Rescue Disk for Windows will assist in ransomware removal. HitmanPro.Kickstart will help remove Ransomware. This post on how to prevent Ransomware will suggest steps to take to stay protected and offer links to ransomware removal tools.
I no use System Restore because my SSD quickly dies after one year.