Remember IrcBot? They could easily connect to Internet Relay Chat as a client, and fool other IRC users as being another user by performing automated functions. But here comes a new addition to this malware family, identified as NgrBot. NgrBot comes with the dangerous ability to destroy data on a user’s hard drive.
The research carried out the Security Research team of Fortinet mentions that this new version of the IrcBot carries new features that are much more harmful than before. It has the capability to join different Internet Relay Chat (IRC) channels to perform various attacks according to the IRC-based commands from the command-and-control (C&C) server.
Watch out for your hard drive
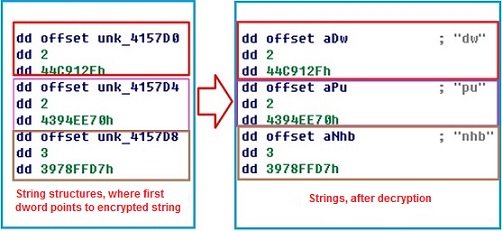
NgrBot can wipe out the hard drives of the compromised systems. The wiping happens as soon as there is any kind of failure in the decryption of its strings. When decrypting, NgrBot uses a string structure where the first dword is a pointer to an RC4-encrypted string; the second dword is the string length; and the third dword is the decrypted string’s CRC32 value.
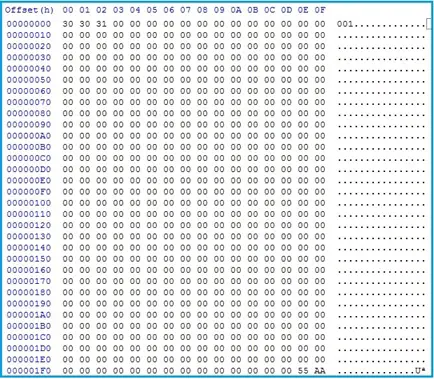
The figure below shows how the overwritten hard disk sector looks like. Post wipe, the attacked system will hang and will be unable to boot.
As if wipe out was not enough, NgrBot also blocks access to antivirus related websites, ensuring that your system cannot avail any outside help. The Security Research blog at Fortinet mentions,
“To do this, the bot injects code into running processes and hooks the following APIs:
- DnsQuery_A (from dnsapi.dll)
- DnsQuery_W (from dnsapi.dll)
- GetAddrInfoW (from ws2_32.dll)
When these APIs are called, the hooking functions check if the address to connect to contains strings that are in the bot’s blacklist”.
The researchers at Fortinet say that until now they have registered two commands received by NgrBot from its C&C server confirming malicious activity. However, expecting the activity to get intense in the near future, the researchers are keeping a track of new active commands from C&C server and maintain a watchful eye on NgrBot’s activity.
Leave a Reply