Both Ransomware attacks and their prevention techniques are becoming more advanced with each passing day. As a result, ransomware attackers have shifted their focus towards human-operated ransomware attacks in large numbers. These days, Microsoft continues to crack down on human-operated ransomware attacks where attackers use handcrafted techniques to exploit vulnerabilities on the computer to gain access to it.
Beware of human-operated Ransomware attacks
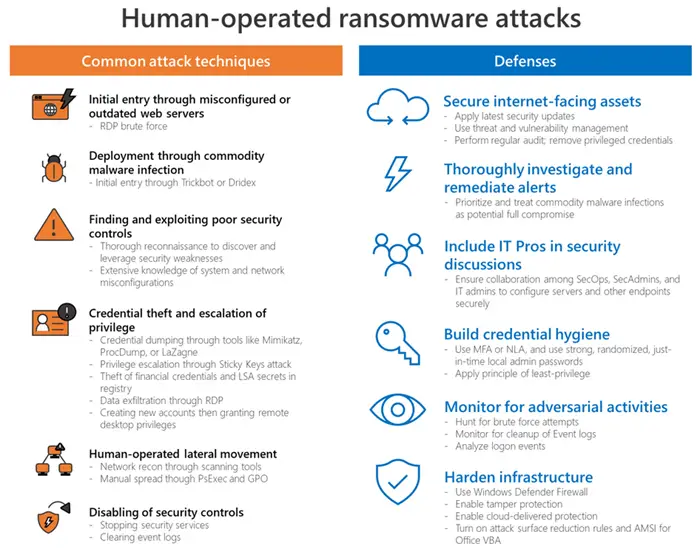
Human errors such as security misconfigurations play a significant role in this type of attack. Microsoft has outlined some of the commonly-used techniques employed in human-operated ransomware attacks:
“Human-operated ransomware campaigns use credential theft and lateral movement methods traditionally associated with targeted attacks, like those from nation-state actors, to deploy ransomware payloads of their choice,” Microsoft said in its recent blog post.
Lateral movement technique is on the rise
Lateral Movement is a technique that attackers use to control remote systems on a network. Since businesses have transitioned to work-from-home arrangements in large numbers, Remote Desktop Protocol (RDP) servers remain vulnerable to ransomware attacks.
Attackers look for the lowest hanging fruits. They will scan everything you have public on the internet and they will look for vulnerabilities and easy ways in, and once they have their first foothold of the organization, it’s very easy to laterally move, said Axis Security’s Gil Azrielant during our brief interaction last month.
Microsoft warns users against some of the common techniques used in human-operated ransomware attacks, as follows:
- Initial entry through misconfigured or outdated web servers using RDP Brute force techniques.
- Deployment through commodity malware infection using Trickbot and Dridex
- Discovering and exploiting poor security controls, weaknesses, and network configurations.
- Credential theft and escalation of privilege, granting remote desktop privileges, data exfiltration through RDP, etc.
- Human-operated lateral movement technique, disabling of security controls, etc.
More often than not, attackers obtain access to target organizations by brute-forcing or exploiting vulnerabilities and security loopholes on internet-facing network devices. That’s why researchers continue to warn businesses against exposing Remote Desktop servers directly to the Internet.
Microsoft has also observed a drastic jump in ransomware operators actively scanning the internet for vulnerable network devices such as gateway and virtual private network (VPN) appliances in the wake of the ongoing crisis.