Inherent loopholes, vulnerabilities and security flaws in operating systems can be exploited by the attackers for their evil motives. SMB file sharing protocol on Windows OS remains one such concern. Having said that, if Windows installations are up to date and fully patched, there’s no danger and you are safe!
Windows Login Credentials can be stolen via Chrome & SCF Files
Shell Command File, better known as SCF is a file format that supports some of the Windows Explorer commands like, Show Desktop that we use on a regular basis. These files when stored on disk, extract an icon file whenever a user tries loading the file in a Windows Explorer window. An SCF file that loads its icon image from an URL poses risks. How? When attempting to load an icon from SMB server, it will prompt for a user’s login credentials. The requests from the SMB server can continue to take place even if users desire it or not.
As a natural consequence, when the user navigates to a folder containing a malicious SCF file, the OS will read the SCF file, make a request to the remote SMB server, and give away the user’s credentials in the form of a NTLMv2, NTLMv1, or LM password hash. Many open-source tools can easily break open these types of password hashes.
Change Chrome browser settings
Google’s Chrome in its default configuration, downloads files without prompting the user for a download location. To avoid this, we can configure the browser to ask us every time where it wants to save each file individually.
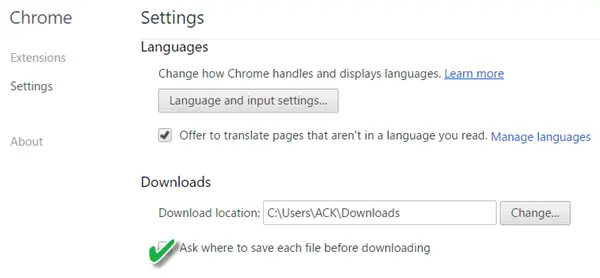
For configuring this, go to Chrome Settings, navigate to ‘Show advanced settings’ section and choose ‘Ask where to save each file before downloading’ option. This way we can remain safe.
Via BleepingComputer.com.
Leave a Reply