A rather shocking news has come from WikiLeaks that the CIA can hack into computers remotely even when the computers are not connected to the Internet. It is a general understanding that whenever a computer cannot be saved from viruses and cyber attacks despite the presence of firewalls, network monitoring services, and antivirus software; the best policy is to disconnect them from the internet network itself. However, WikiLeaks says it is now possible to hack the computer even when it’s disconnected from the network and the internet.
Document on Brutal Kangaroo by WikiLeaks
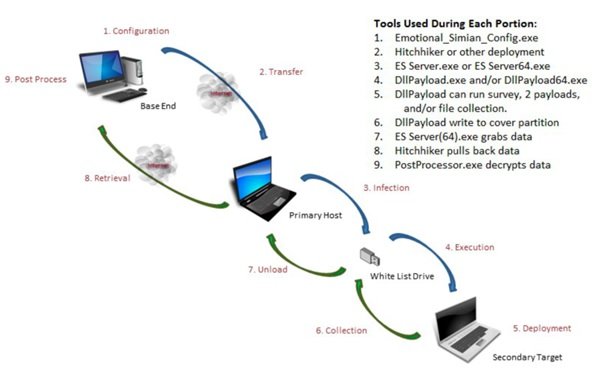
It is possible to hack a computer not connected to the Internet with the software such as Brutal Kangaroo. According to the document published by WikiLeaks on June 22nd, 2017, Brutal Kangaroo is a project of the CIA. This is a tool suite for Microsoft Windows that targets closed networks by air gap jumping using thumb drives. Basically, Brutal Kangaroo components create a custom covert network within the target closed network and providing functionality for executing surveys, directory listings, and arbitrary executables.
The WikiLeaks document further describes how a CIA operation can pass through a closed network within an organization or enterprise without direct access.
The Brutal Kangaroo software first infects an Internet-connected computer within the organization. This computer is called as the “primary host”. On this primary host, the software installs the BrutalKangaroo malware. When the user inserts a USB stick into the primary host to copy any data, the thumb drive gets infected with the malware. Soon, when the user uses the same USB into another computer within the closed network this new computer too, gets infected. By browsing the USB drive with Windows Explorer on such a protected computer, it also gets infected with exfiltration/survey malware.
WikiLeaks mentions that this malware can now control the infected PCs within the closed network. If several such computers on the closed network are under CIA control, they form a covert network to coordinate tasks and data exchange. WikiLeaks further stated that though it is not clearly mentioned, this method of compromising closed networks is very similar to how Stuxnet worked.
As WikiLeaks stated, the major reason behind this flaw is people forget to isolate the sensitive computers. Even the slightest chance or the air gap around these computers is enough for the Brutal Kangaroo malware to take over. However, it will never be a case when nothing is copied from these computers. Many times there are patches and updates to be installed on these computers, which can make way for the hackers to control these computers.
To know more about the Brutal Kangaroo document released by WikiLeaks, visit this link. Via qz.com.
WHO are watching the WATCHERS in our Government? Hopefully, PRESIDENT TRUMP IS.
DRAIN THE SWAMP AND GET RID OF ALL HOLDOVER/LEFTOVERS WHO WERE HIRED AND APPOINTED BY BARACK INSANE OBAMA.
THANK GOD WE HAVE TRUMP.
MAGA!