Cyberthreat has only grown stronger and more complex over time reveals latest Cisco 2014 Annual Security Report. It now appears more mature, far-reaching and most importantly, well-funded. Why? The inclination of gadget-friendly generation more towards mobile and cloud technologies balanced by acute shortage in skilled security professionals to manage such vulnerable platforms.
Moreover, cybercriminals seems to have learned harnessing the power of Internet infrastructure well. It promises more benefits than simply gaining access to individual computers or devices. Attacking methods have become more sophisticated or advanced like hide-in-plain-sight infiltrations, and exploitation of the trust required for economic transactions, government services and social interactions.
Increased complexity of threats and solutions due to rapid growth in intelligent mobile device adoption and cloud computing provide a greater attack surface than ever before. New classes of devices and new infrastructure architectures offer attackers opportunities to exploit unanticipated weaknesses and inadequately defended assets”, the report outlines.
Cisco 2014 Annual Security Report
The report brings out 3 important points:
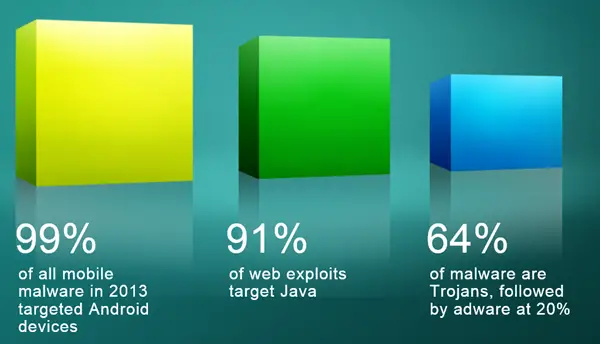
- 99% of all mobile malware in 2013 targeted Android devices
- 91% of web exploits target Java
- 64% of malware are Trojans, followed by adware at 20%
The report sheds light of 3 key issues namely,
- A greater attack surface area: Cybercriminals have found multiple ways as inroads to the network and therefore the ultimate destination: the data center, where high-value information resides.
- The proliferation and sophistication of the attack model: Even basic Internet infrastructure services—including web hosting servers, nameservers, and data centers—have become key targets for hackers who want to launch increasingly larger campaigns.
- Complexity of threats and solutions: Monitoring and managing information security has become a challenge of sorts for security teams. Point-in-time solutions long-relied upon by organizations for cybersecurity are simply inadequate and at times, ineffective.
Cisco has invested considerable time, effort, and money in the effort to make our products robust enough for deployment as trustworthy systems.
One of the less complicated graphics freewares I tinker with, and help and get helped by others with, is JWildfire, a varietal of fractal generators; it is of course dependent on JRE 6 or greater as its rendering environment. Your report will help show some why I constantly test my own security layering (and have it tested by others) in re using JWildfire, and why I recommend such artists use a security configuration at least equivalent to mine (no exploits or such in over a year, knock wood!).