A CCleaner version that was available for download during the period 15th August and 12th September was compromised and hacked to distribute the Floxif malware. According to Piriform, its developers, the affected versions were CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191.
Said Piriform, the developers of CCleaner, which was bought over by Avast earlier:
A suspicious activity was identified on September 12th, 2017, where we saw an unknown IP address receiving data from software found in version 5.33.6162 of CCleaner, and CCleaner Cloud version 1.07.3191, on 32-bit Windows systems. Based on further analysis, we found that the 5.33.6162 version of CCleaner and the 1.07.3191 version of CCleaner Cloud was illegally modified before it was released to the public, and we started an investigation process. We also immediately contacted law enforcement units and worked with them on resolving the issue.
This incident was found by Talos:
Talos recently observed a case where the download servers used by software vendor to distribute a legitimate software package were leveraged to deliver malware to unsuspecting victims. For a period of time, the legitimate signed version of CCleaner 5.33 being distributed by Avast also contained a multi-stage malware payload that rode on top of the installation of CCleaner.
They have also uploaded a diagram describing the high-level operation of this malware :
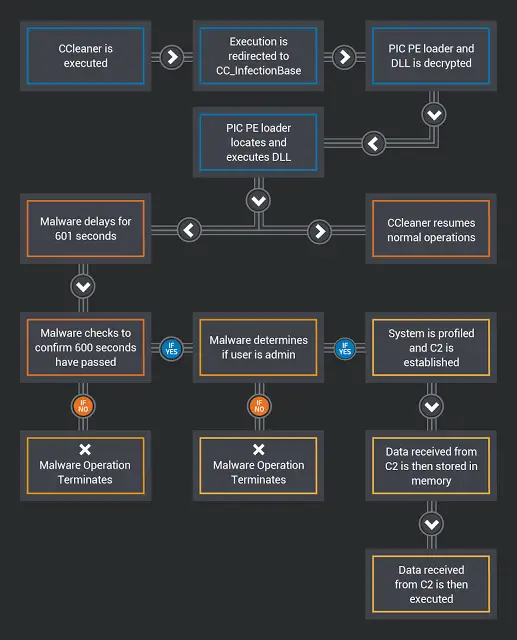
CCleaner has over 2 billion downloads worldwide, and so The impact of this attack could be severe. So if you are using this version, we recommend that you uninstall it from your computer asap and update to the latest version which is currently v5.34. Having done this, make sure you scan your full computer with your antivirus software.
Piriform is not aware of, nor speculating how the unauthorized code appeared in the software, where the attack originated from, how long it was being prepared and who stood behind it.
I just got an alert that Ccleaner has a newer version than the one mentioned in this article. It is version 5.35.6210. I’m wondering if I should wait to download it? I’ve used Ccleaner for years, and I will continue to. I trust Piriform, but they are obviously not infallible. As for Avast… if they were who was distributing the malware version, how could they not detect it? They are an anti-virus software company! This is very disturbing, because I use the Avast AV on my computer.
It think it might be safe to download the newer version. I plan to do so too.:)