As if Cryptolocker, the ransomware was not enough to target computers running Microsoft Windows, we have a new clone of it called Critroni that uses private key mechanism similar to Cryptolocker to attack computers.
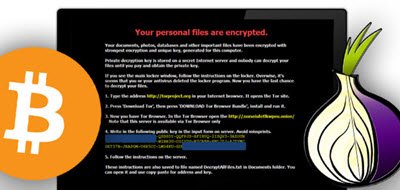
Cryptolocker, if you remember is a type of malware used to encrypt important files on a PC with a unique private key only known to the attackers. The encryption further leads to the development of a new piece of extortion-ready malware. The process of encryption may take several days depending on the amount of data exposed to malware.
Then, upon completion, Cryptolocker displays a note demanding ransom. It also makes visible to the victim a timer that prompts him to take some action i.e. agree to the demands of malware developer to get the private for unlocking encrypted files before his data is gone forever.
Critroni – A new CryptoLocker Ransomware Clone
Building upon the same ingenious idea, we have a new and more deadly variant of Cryptolocker called – Critroni.
Critroni, drops a spambot on victims’ machines first. Then, the spambot downloads a couple of other payloads, including Critroni. Once on a victim’s PC, Critroni encrypts important files, like photos and documents, and displays a dialogue box that prompts the user to take an action for freeing his system from the potential threat and make a payment in return (in Bitcoins or via some different mode as described by the attacker).
Fedor Sinitsyn, senior malware analyst, told Threatpost,
It uses C2 hidden in the Tor network. Previously we haven’t seen crypto-malware having C2 in Tor. Only banking Trojans. Executable code for establishing Tor connection is embedded in the malware’s body. Previously the malware of this type, this was usually accomplished with a Tor.exe file. Embedding Tor functions in the malware’s body is a more difficult task from the programming point of view, but it has some profits, because it helps to avoid detection, and it is more efficient in general.”
Leave a Reply