Dr. Web one of the well-known anti-virus company from Russia has come up with a report that has studied one of the most widespread threats in April 2013, the Trojan.Mods.1.
Trojan.Mods.1 works by intercepting the system functions necessary for translating DNS names to IP addresses. It does so via a special algorithm. The effect of this is that instead of the site the user has requested, he is redirected to fraudulent pages or certain group of addresses that seek your personal information, such as your mobile phone number and reply to an SMS sent from the short number 4012. If complied with, a certain amount is debited from their account.
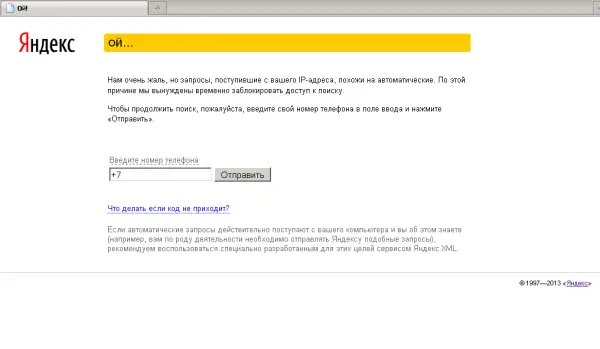
Earlier known by the name Trojan.Redirect.140 the trojan has 2 components:
- The dropper
- Dynamic Link Library
These two components store the payload. During the Trojan installation the dropper duplicates one of its copy into a folder located on your computer hard drive and executes itself without your consent. It can be launched as a Java update – but requires user confirmation first, to bypass the User Accounts Control prompt.
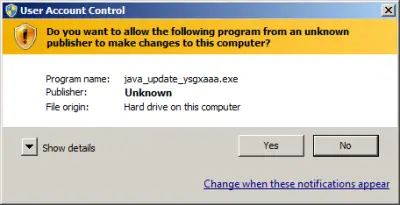
Once this procedure is completed successfully, the dropper saves the main library on the hard drive. The main library then starts its dirty tricks, injecting or transferring its code into all the processes, running currently on an infected computer. The configuration file required to run Trojan.Mods.1 is encrypted and stored in the dynamic linking library.
The codes injected are operational in the processes of the following browsers:
- Microsoft Internet Explorer
- Mozilla Firefox
- Opera
- Safari
- Google Chrome
- Chromium
- Mail.Ru Internet
- Yandex.Browser
- Rambler Nichrome
Dr.Web has updated its virus database to fight off this threat – I am sure that most other antivirus companies must also have followed suit.
Stay safe online! Follow some basic tips to secure your Windows computer!
Leave a Reply