Dharma Ransomware now officially has decryptor keys. Kaspersky RakhniDecryptor v 1.17.17.0 & ESET Crysis Decryptor v 2.0.3.0 have been updated to decrypt Dharma ransomware encrypted files and remove the malware.
Kaspersky has tested and legitimized the master decryptor keys that were leaked online on some forums. The company has certified the use of these keys to access Dharma encrypted files. These new decryptor keys have also been included in their RakhniDecryptor and have been tested by security analysts to successfully function in the perfect manner. If you have been a victim of Dharma Ransomware and need access to the encrypted files, here’s a quick guide to using these decryptor keys.
Decrypt Dhara Ransomware encrypted files
1. All files attacked by this specific ransomware can be detected with the file extension ‘.dharma’ on the target files.
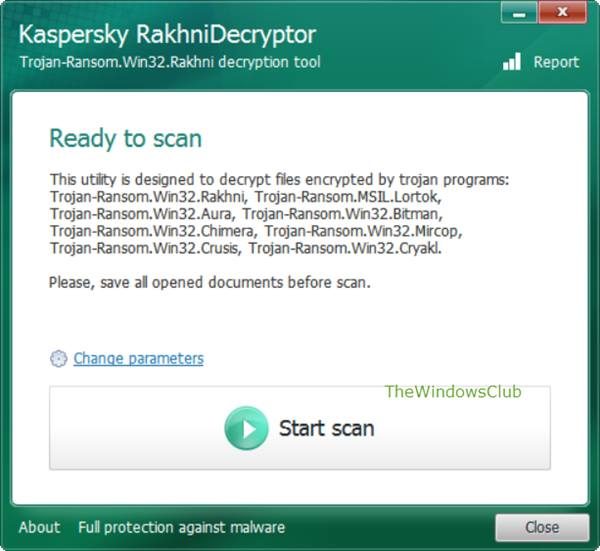
2. After detection of all the affected files, you can download the RakhniDecryptor software. Once downloaded, extract the file and run it to open the main screen of the program.
3. Check or update to version 1.17.17.0. This is the latest version of the software, which contains the updated Dharma decryptor keys.
4. Click on the Start Scan button and select a Dharma affected file from the prompt window. Be sure to NOT select a text file as RakhniDecryptor is unable to decrypt other files using that format.
5. Once the file is selected, the software will run a full scan on the entire system and detect all the other Dharma encrypted files available on the hard disk. It will then start the reversal process.
6. After a few minutes of scanning, the RakhniDecryptor will display all the files that have been scanned and decrypted. You can also access a drop-down menu with a detailed list of all files and programs treated in the process.
7. You can now access all the encrypted files properly. All the affected files will have a .dharma encrypted copy left behind, which you can delete from the system manually or use CryptoSearch.
This online leak and further confirmation, from Kaspersky, of the decryption keys, comes as a boon for Dharma victims that have been left with a financial loss as well as no access to their files. The source of the leak is unknown but usually, comes from users from the attacking side gone rogue. So, if you have been affected by Dharma or any other ransomware and left with encrypted files; holding onto them makes sense as the keys will be made available sometime in the future.
Take a look at this post that lists a bunch of Ransomware Decryptors that are currently available.
Leave a Reply