Malware attacks have consistently been on the rise for the past several years. Now these days, attackers try out different ways to gain unauthorized access to your digital lives. Malware spreading via email phishing is common. But now, email phishing has also become difficult due to many advanced security and filtration techniques adopted by cybersecurity companies and email services. Since smartphone consumption has reached its peak, attackers have largely shifted focus towards SMS communication.
Emotet malware uses SMS text messages
Researchers have discovered that Malware infiltration via SMS has become extremely common these days. However, SMS malware + phishing combination is a deadly combination by all means. One such malware – Emotet – has consistently been a headache for general users and organizations in both the private as well as public sectors.
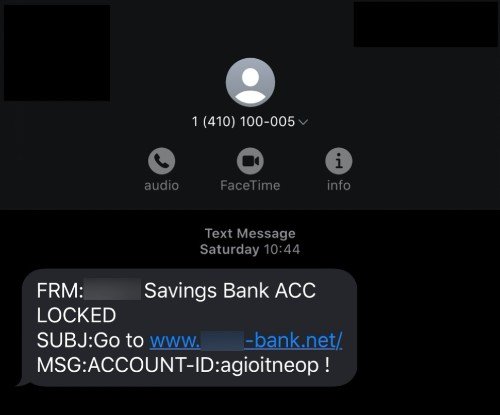
Security experts have discovered an SMS phishing (also known as SMiShing) campaign, which is targeting mobile numbers in the United States. The aim is to gain unauthorized access to users’ online banking credentials and install Emotet malware. In this campaign, attackers impersonate major US banks and alert users about a locked account over an SMS message.
More often than not, an SMS message like this includes an embedded URL that sends users to malicious phishing websites. However, researchers warn that the same technique can also be used to trick users into installing Emotet. Researchers have also addressed the possibility that this could very well be a part of the targeted campaign to drop TrickBot payloads to infected devices.
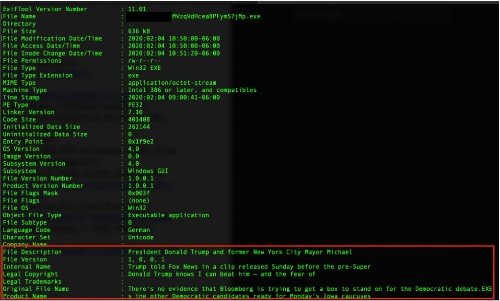
As researchers explain, Emotet manages to evade malware detection tools. Sometimes attackers add “news” excerpts into infectious binary files, which is a common anti-detection tactic. See the screenshot below:
Commenting on the discovery, the IBM X-Force researchers had this to say:
“Visually, the potential victim sees a customized phishing page that mimics the bank’s mobile banking page with a domain that was registered on the same day by those distributing Emotet. The domain features the bank’s name with a different top-level domain (TLD) and is likely designed to grab the victim’s credentials as a first step and then have them download a document file loaded with malicious macros.
Our researchers found the file on the distributing domain and looked into some obfuscated malicious PowerShell scripts that led us to additional Emotet-serving domains.”
How dangerous is Emotet malware?
Originally designed as a banking malware, Emotet can steal your private information and evade detection by anti-malware tools. That’s what makes Emotet even more dangerous, to begin with. Meanwhile, the US Department of Homeland Security (DHS) has also concluded that Emotet is one of the most expensive and harmful malware.
In the past, Emotet has affected both the government and private sectors. Bad to worse, every Emotet incident has cost SLTT governments as high as $1M to fix!
You can also check out the EmoCheck Tool that keeps a tab on Emotet malware infection.