You may have experienced a situation, where a site may have asked you to install a third-party software like Adobe Flash Player or Silverlight, in order to be able to view a video. taking advantage of this familiarity factor, some malicious ads are enticing web surfers to download and install a fake free Media Player, which is being distributed via a rogue Adobe Flash Played advertisement.
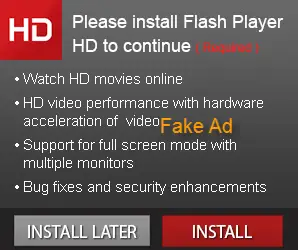
Webroot a well-known security company, picked up such ads which were being distributed through the YieldManager Ad Network. The ads exposed surfers to a fake Adobe Flash Player. It asked users to download and install an Adobe Flash Player HD in order to watch HD movies online.
Once users clicked on the ad, they were presented with a rogue free Media Player page. There was no damage to the users till this time. But those users who fell victim to this and clicked on the free Download button, ended up having malware and potentially unwanted software on their computers.
The day this rogue ad was found, only 8 out of 46 antivirus software had the capability to detect this rogue media player – also called as Somoto BetterInstaller; Adware.Somoto/TROJ_GEN.F47V0429, says Webroot.
The affiliate network participant that’s abusing the YieldManager ad network is currently earning revenue through the Somoto’s BetterInstaller PPI (Pay-Per-Install) revenue sharing network.
Stay safe!