As if WannaCrypt was not bad enough! We now have another Ransomware threat to deal with in the form of SOREBRECT. Security software company, Trend Micro, discovered SOREBRECT couple of months ago where it was found to have infected systems and networks of organizations in the Middle East.
Fileless ransomware
SOREBRECT is a Fileless malware which injects malicious Code with unconventional encryption techniques. It exploits the PsExec utility in Windows to force code injection, and at the same time focus on remaining stealthy.
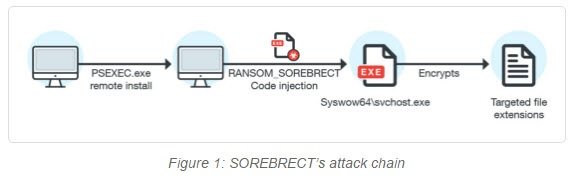
What makes SOREBRECT deadly is its self-destruct routine that eventually turns it into a file less threat. The ransomware injects code into a legitimate system process (which executes the encryption routine) before terminating its main binary. To ensure that security researchers don’t track its activities, SOREBRECT deletes the infected system’s logs and other artifacts, including their timestamps (i.e. appcompat/shimcache and prefetch).
As per Trend Micro, when first discovered, SOREBRECT had a low distribution and concentrated mostly on Middle Eastern countries like Kuwait and Lebanon. However, now, it has spread to Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S.
Industries including manufacturing, technology, and telecommunications are on the ransomware’s radar and given its unique coding; there are fears about SOREBRECT spreading to other parts of the World, or even in the cybercriminal underground where it can be peddled as a service.
How does SOREBRECT infect PCs
SOREBRECT’s abuses PsExec, (a legitimate, Windows command-line utility that lets system administrators execute commands or run executable files on remote systems) to execute commands or run executable files on remote systems.
Trend Micro says,
“The misuse of PsExec to install SOREBRECT indicates that administrator credentials have already been compromised, or remote machines were exposed or brute-forced”. It injects its code into Windows’ svchost.exe process, while the main binary self-destructs. The combination is potent: once the deployed ransomware binary finishes execution and self-termination, the injected svchost.exe—a legitimate Windows service-hosting system process—resumes the execution of the payload (file encryption)
Further, it utilizes wevtutil.exe to delete the system’s event logs, and vssadmin to delete shadow copies so that it cannot be traced.
SOREBRECT can also encrypt networks
SOREBRECT can infect files on the other computers connected to the infected PC through the local network. It scans the network for asset discovery and enumerating open shares—folders, content or peripherals (i.e. printers) that others can readily access through the network.
To stay protected, restrict user write permissions and limit privileges for PsExec. Keeping a backup of the files is a must. Keep the system and network updated as it reduces the risks considerably.
Leave a Reply