Background Intelligent Transfer Service, also known as BITS, is one of the Windows OS’s core features. It assists the Operating System in using idle network bandwidth to download necessary files. Now, reports claim that hackers are trying to use the BITS feature to download malicious payload to Windows systems by evading the firewall protection.
Attackers use Windows BITS
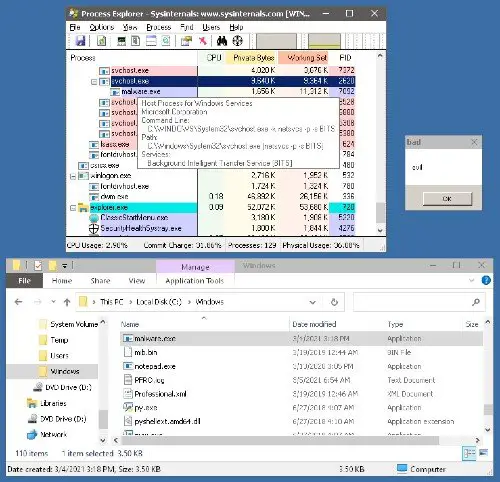
The new hacking technique works because activities done through the BITS job container can stay exempt from Windows Firewall surveillance. The Mandiant cyber forensics arm of FireEye found this during their analysis of several attacks last year.
In particular, researchers at FireEye looked at a phishing campaign that had affected hospitals and medical centers in 2020. This campaign had installed a custom backdoor on the infected systems, and the RYUK ransomware attack later used the same to get into the PC. The new research indicates that the hackers may have also used the BITS feature to download the payload for the ransomware attack.
The study adds that hackers designed the malware to use BITS under further disguise. Instead of creating a new process, it used host processes to download payload from malicious websites. This method also prevented the firewall from looking into the contents of the downloads.
FireEye researchers include in their statements that the RYUK ransomware attackers had used BITS to keep in touch with the infected systems. It shows that the decision to use BITS for the attacks was thought-out and tested by the group. In this particular case, the attackers set up BITS to download an unknown file from the system’s localhost.
It then launched the KEGTAP backdoor, allowing inside the ransomware elements. It is not clear whether the attackers had used the privileges given to BITS to evade other security features of Windows. Considering that BITS has been a part of the Windows OS since XP, it is a possible scenario.
Microsoft is yet to respond to these findings from FireEye, but it is expected to do so very early. However, until then, users can rely on the BitsParser utility released by FireEye. This Python-based utility will prevent attackers from manipulating the BITS database with fake/nonexistent job information.