These days, cyber attackers continue to imitate government agencies and authorities worldwide to further their malicious phishing activities in large numbers. Recently, we saw how new phishing campaigns impersonating the World Health Organization (WHO) are on the rise, in the wake of the COVID-19 outbreak.
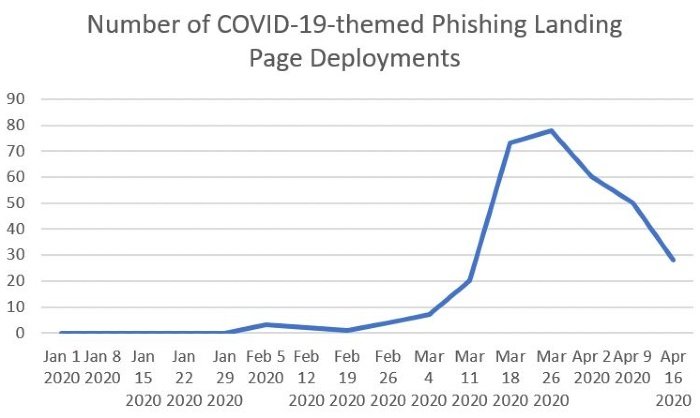
Attackers use ready-made phishing templates
A new report by a cybersecurity company Proofpoint highlights a sudden increase in the number of COVID-19 phishing landing page deployments since March 2020:
“Credential phishing attackers often tailor their email lures with themes they believe will be the most effective and use general websites for actual credential harvesting.”
Attackers continue to use the on-going panic to their advantage. Since March 2020, researchers have observed a surge in the deployment of COVID-19-themed phishing website templates impersonating NGOs including the WHO, Internal Revenue Service (IRS), among others.
Since January 2020, security researchers have observed over 300 phishing campaigns worldwide. Half of these attacks targeted user credentials. Researchers have also shown some of the recent template examples that make it easy for threat actors to deploy malicious phishing websites, impersonating well-known authorities.
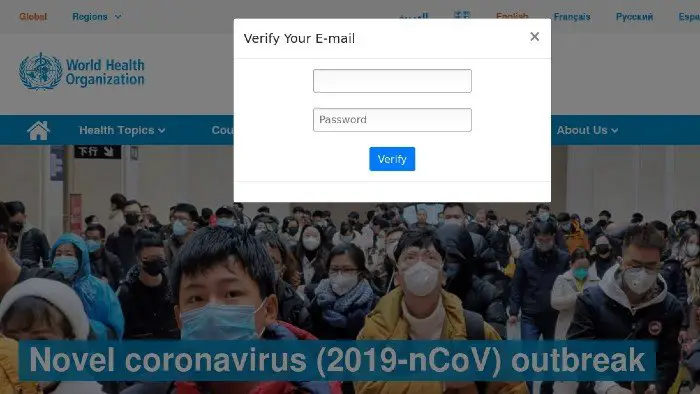
The report denotes a sluggish growth that significantly jumped at the beginning of March 2020 and then began to plunge in April 2020.
“The peak in March and subsequent drop off in April likely reflects a combination of saturation for COVID-19 payment theme phishing templates and a move towards other COVID-19 themes as many one-time payments were disbursed.”
COVID-19-themed frauds and scams are not new. Earlier, researchers observed a 30 percent increase in the number of COVID-19 related cyberattacks during a single week.
Attackers use the email subject line such as “Urgent letter from WHO: First human COVID-19 vaccine test/result update” to lure victims, asking them to enter Google/Facebook login credentials.
While the majority of phishing campaigns are primarily in English, researchers have also seen campaigns in Japanese, Spanish, Italian, French, Portuguese, Turkish, and other languages.
These fake phishing websites ask users to verify their login credentials by entering their username/email addresses and passwords. Once users enter their login credentials, it would compromise multiple accounts since the majority of users tend to use the same passwords on multiple websites.
In related news, threat actors have been abusing Google search’s open redirect feature to promote their phishing campaigns.
Leave a Reply