IoT or Internet of Things is a relatively new concept and is currently catching up with consumers around the world. But with any kind of upcoming technology comes the risk of frequent malware attacks. In fact, 2015 was a record year in terms of malware attacks on IoT devices. A majority of the attacks came from countries including Russia, USA, Germany, and China.
IoT devices being used for DDoS attacks
The root cause of these frequent attacks is the lack of proper or biometric security features on these IoT devices. For instance, you wouldn’t expect your smart refrigerator or washing machine to have a fingerprint sensor to unlock its features; it’s just impractical. With the lack of a proper interface, it might not be possible to even detect an attack on your device, in the first place.
A lot of these devices just require a basic setup and installation and may even not get firmware updates throughout their life cycle. This helps attackers easily push on malware to them and get into the central system.
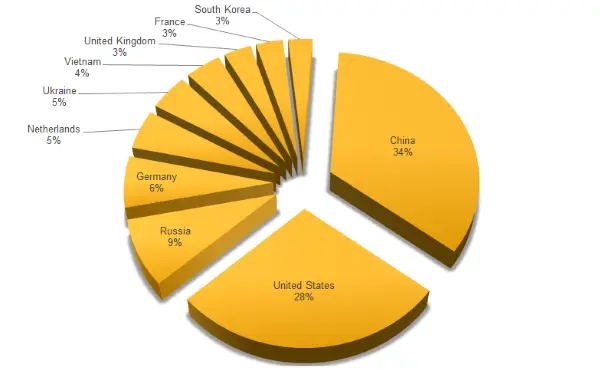
Symantec carried out a thorough analysis of these issues and found out some interesting revelations. One of them claims that most of the DDoS attacks on these devices are coming from China & US, followed by Russia and Germany. Although an important thing to note is that these figures represent the location of IP addresses used to launch malware attacks on Symantec’s honeypot. In some cases, IP addresses used might have proxies used by attackers to hide their true location.
Attacks on Symantec’s honeypot also revealed what the most common passwords IoT malware used to attempt to log into devices. Not surprisingly, the combination of ‘root’ and ‘admin’ leads the chart, indicating that default passwords are frequently never changed. The default Ubiquiti credentials (user name: ubnt and password: ubnt) also feature highly, claims Syantec.
You can read the report and their extensive analysis here.
Leave a Reply