If you are using Kaspersky Security Suite, there is some good news for you. You are using the best Anti-Virus in the world, according to this report. In the latest testing done by AV-Comparatives, the independent, non-profit organization which tests security suites, Kaspersky has topped the testing process.
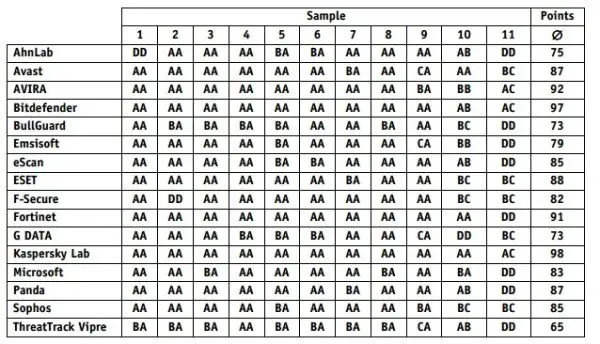
AV-Comparatives tested many of the popular malware removal tools, which include AhnLab, Avast, Bitdefender, Bullguard, Emsisoft, eScan, ESET, F-Secure, Fortinet, G Data, Kaspersky Lab, Microsoft’s Security Essential, Panda, Sophos and ThreatTrack Vipre. The results are for the month of November 2013 on the Windows 7 x64 operating system. In the test, many widespread trojan horse, worm, backdoor, ransomware, etc, were included.
Kaspersky has topped the testing with securing 98/100 points, followed by Bitdefender which secured 97 points, AVIRA secured the third position with 92 points.
The test also mentions which of the security firms provide free malware removal tools. AhnLab, Bullguard, Emsisoft, Fortinet and ThreatTrack were among the ones which did not offer Boot-Disk on their websites. A Boot-Disk or Bootable antivirus rescue disk is the disk-image file which enables a user to boot the computer through that image file, making the existing operating system(s) not interrupt the process, and establishing a complete control over the computer’s hard-drive(s).
From the press release, it is clear that many security firms, including and especially AVG and Norton didn’t participate in the testing. AV-Comparatives only include those vendors which signed up for this testing.
The PDF available on the website provides more information about the testing procedure, the kind of malware which were used, and more data, which security firms can use to improve their service.
Kaspersky Internet Security is available at the Kaspersky Store or at Amazon
too. Incidentally, users of Kaspersky Internet Security are protected against all current modifications of the CryptoLocker ransomware, preventing it from executing on their systems.
Let us know where your security software figured on this list.