Another day, another malware, this has been pretty much the norm with so many malware and ransomware cropping up on daily basis. The latest one is detected by CyberX’s threat intelligence research team and it has now uncovered evidence that the KillDisk disk-wiping malware which was earlier used in the cyber attacks against the Ukranian power grid has now been shaped into a Ransomware.
KillDisk Malware turns Ransomware
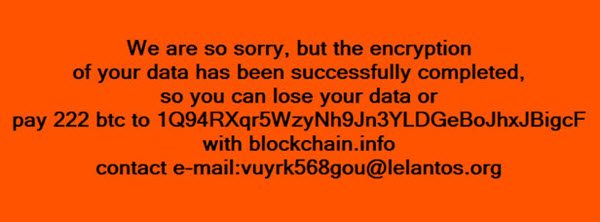
The security researchers reverse-engineered the new malware variant and also found that it displays a pop-up message which demands 222 Bitcoins or nearly 4206000 in return for the decryption key. The threat seems to be aimed at industries and corporations for whom the data means everything and will not hesitate to cough up the ransom.
The new malware is said to affect both local hard drives and also any other network mapped folders that are shared, thus eventually ensuring that it spreads to an entire organization.
The Ransomware makes use of RSA 1028 public key and AES shared the key in order to encrypt the drive and thus each encrypted file will be having its own AES key. The attacker’s contact email doesn’t reveal much since it just used an anonymous email in order to protect the identity of the attackers. Like most of the malware lately, the new malware is also been suspected to be delivered via Office attachments.
It’s said that the new Malware is the handiwork of TeleBots gang which in essence is a group of Russian cyber criminals who have been evolved from the Sandworm group, a group that was responsible for a group of attacks in the United States during 2014. Furthermore, it is also suspected that the cybercriminals are targeting chemical plants in eastern Europe for easy extraction. FBI has pegged the Ransomware industry at a staggering $1-Billion in 2016 and its prime targets have been the industries which will help them to monetize easily, says the blog post.
Have a safe new year!
Leave a Reply