The potential dangers of storing all your important passwords in a single place have been exposed by a most recent attack against LastPass users. The Phishing attack, it is reported does not require any special skills but exploits the existing flaws in the design elements of the password manager’s core functions. The attack allows the attacker to take full control of LastPass user’s email, password, and even two-factor authentication code, giving full access to all passwords and documents stored in LastPass.
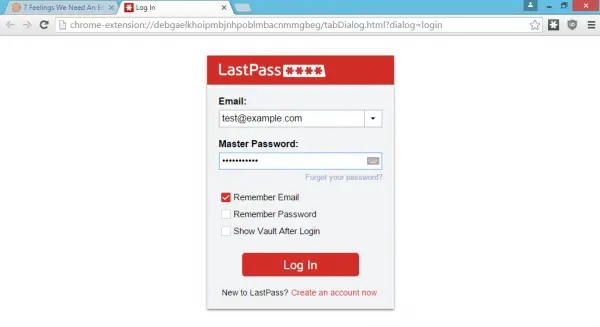
LastPass Phishing Attack
Since the notification is displayed in the running browser viewport, the attacker can trick a user and throw a fake notification which looks extremely similar to LastPass’s original notification. A user fails to discern the difference between the original and the fake notification since It’s pixel-for-pixel the same notification and login screen.
When a victim unaware about the attack visits any malicious website or an authentic/genuine website vulnerable to XSS, the attacker deploys a script lostpass.js from Github. The script runs a scan verifying if the user has LastPass installed on his machine. If yes, the script will pop-up a login expired notification requesting the user to re-login.
Upon clicking the notification, the user is transferred to a LastPass login page and after entering the required credentials he authorizes the attacker to use LastPass API to check the validity of entered information via his own servers.
Here are some suggestions to stay safe:
- Log all logins and failures
- Disable mobile login
- Ignore notifications in the browser window
- Enable IP restriction
- Inform your employees of this potential attack.
If the user has a two-factor authentication enabled, he will be redirected to the two-factor authentication page. If the entered credentials (username and password) are found to be correct the attacker downloads all of the victim’s information from the LastPass API in no time. Thereafter, he can install a backdoor in victim’s account, add the attacker’s server as a “trusted device” and try other sorts of nefarious tactics.
The vulnerability ahs been patched now.
See: https://lastpass.com/support.php?cmd=showfaq&id=10072 For the real story and the fixes in place.