Recently, a new ransomware was detected by Microsft, which could be a huge threat to Windows users. According to Microsoft Malware Protection Center, this new malware Ransom:Win32/ZCryptor.A shows worm-like behavior. Moreover, this ransom leverages removable and network drives to spread itself and affect more users.
Link (.lnk) to Ransom
“This ransomware can stop you from using your PC or accessing your data. It is distributed through the spam email infection vector. It also gets installed in your machine through other macro malware, or fake installers (Flash Player setup)”.
Microsoft’s team further mentions some more information on this new ransomware on its official blog,
The infection vector for this new ransomware identified as Ransom:Win32/ZCryptor.A is spam emails. It is distributed through spam emails and gets installed in the user’s machine using other macro malware. The ransomware may use fake installers like a Flash Player setup or an encryption program.
The ransomware carries ZCryptor and executs it when it gets installed on the user’s machine. Once this is done, it will make sure it runs at start-up:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run zcrypt = {path of the executed malware}
The worst part is, this new ransomware also drops autorun.inf in removable drives, a zycrypt.lnk in the start-up folder:
%User Startup%\zcrypt.lnk
Besides this, it also drops a copy of itself as {Drive}:\system.exe and %appdata%\zcrypt.exe, and changes the file attributes to hide itself from the user in file explorer. It may change itself to c:\users\administrator\appdata\roaming\zcrypt.exe.
Once all this is done, the ransomware will start displaying a warning message in a dropped HTML file How to decrypt files.html. The warning message looks as follows:
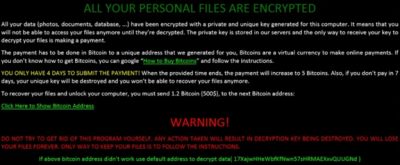
Microsoft’s team is extremely cautious about this new ransomware and the team is making the users also aware of its symptoms and consequences.
You can read more about this at Microsoft Malware Protection Center.
Leave a Reply