The infamous Locky ransomware has struck again. Released in February 2016, the ransomware had affected all versions of Windows OS, such as Windows XP, Windows Vista, Windows 7, Windows 8, and even Windows 10. The ransomware is now back with a bang in the form of a spam campaign that is asking the victims for unpaid debts. The majority incidences of Locky ransomware were recently found in Japan, South Korea, and the USA.
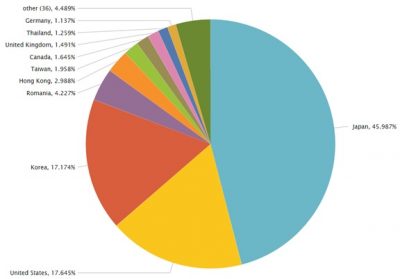
Effects of Locky ransomware
The ransomware’s spam activities were found to be stopped until June 1st, 2016. However, on June 21st, 2016 it was found by FireEye’s Dynamic Threat Intelligence (DTI) that the activities of Locky have increased. The ransomware now contains JavaScript within its spam emails. The new attack was identified as new Locky ransomware spam campaign.
Locky is a ransomware that infects victim’s computer by downloading its files. Once infected, the Locky ransomware scans all the drives and network shares for targeted file types and encrypts them using the AES encryption algorithm. After the encryption, the victim is not able to access them using the regular programs. After infecting victim’s computer, the ransomware also changes the desktop wallpaper to something that resembles a ransom note. Till now, Locky ransomware has been distributed in the form of spam email.
The spam email talks about an unpaid invoice that is attached along with the email. It’s a ZIP archive that contains Locky downloader written in JavaScript. A typical Locky ransomware spam email looks as follows:
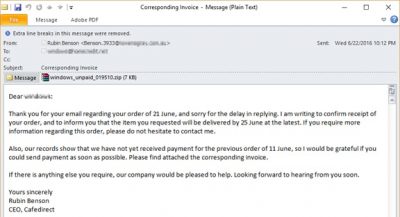
FireEye’s team has identified some new updates in the latest ransomware spam emails. The team has mentioned what the JavaScript downloader does when Locky ransomware is downloaded onto the victim’s machine.
- It iterates over an array of URLs hosting the Locky payload.
- If a connection to one of the URLs fails, the JavaScript sleeps for 1,000 ms before continuing to iterate over the array of URLs.
- It uses a custom XOR-based decryption routine to decrypt the Locky payload.
- It ensures the decrypted binary is of a predefined size. In Figure 4 below, the size of the decrypted binary had to be greater than 143,360 bytes and smaller than 153,660 bytes to be executed.
Unfortunately, Locky ransomware spam campaign is still ongoing. Now it has also added anti-analysis / sandbox evasion technique. FireEye’s team has ascertained that they will remain vigilant in order to protect their customers.
You can read the complete report on Locky ransomware on FireEye’s threat research blog.
Leave a Reply