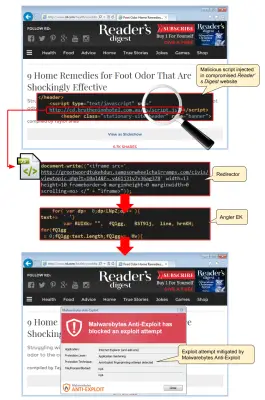
A majority of content-centric sites across the Internet are running on WordPress. There are reports that the Angler exploit kit has compromised many WordPress sites either directly or indirectly. The attack was carried out by injecting a malicious script within compromised WordPress sites which will take the users to another URL. The primary intent of the attack is to load the Angler exploit kit.
One of the victims of the attack has been Readers Digest, one of the popular website. Readers who visit the website need to cross check and make sure they are not infected. Site owners on the other hand need to tread carefully as the injected scripts/URLs will keep on varying in spite of making use of the same pattern.
Malwarebytes, a security research firm has observed that at the time of their inspection the payload was the Bedep which in turn loaded a backdoor Trojan called Necurs, that being said this can change at regular intervals.
The firm had warned Readers Digest of the exploit but didn’t receive any response from them, the site however continued delivering the malware.
At the time of writing, the site is still delivering malware. We hope that by making this public we will raise awareness and prevent unnecessary infections.
People need to take the necessary precautions while visiting any sites. The injected string duplicates itself and can be found in the process bar names as “notepad.exe”. Killing the process or the process tree won’t be of much help as it will be reinitiated shortly.
Here are some tips that will help you protect and secure your WordPress site. Meanwhile you as a user should always exercise caution when on the web, and use a good security software.
Leave a Reply