The exponential rise in the value of the cryptocurrency has many sides to it. While most of us are impressed with the futuristic technology, the flip-side of cryptocurrency cannot be ignored. Cybercriminals are leaving no stones unturned when it comes to giving cryptocurrency a bad name. The cryptocurrencies inadvertently end up shielding the identity of criminals especially since it is easier to transfer bitcoin privately as opposed to money or even hard cash. The rise in the value of Cryptocurrency has also driven up the cryptocurrency crimes, especially ones related to Bitcoin.
All these factors combined, the cryptocurrency world is currently flooded with fraudsters, cybercriminals, unethical crypto miners and what not. As per Microsoft’s latest research the malicious crypto mining programs are on a steady rise. In fact on March 6, Windows Defender Advanced Threat Protection successfully blocked a massive coin mining campaign from a group that referred to themselves as Dofoil.
Cryptocurrency related cybercrimes are on the rise
The Windows Defender ATP aims at providing the best security features which include behavioral analysis, and cloud-powered machine learning. The machine learning bit is expected to help in tackling the increased threats of coin miners including Trojanized miners, mining scripts that are hidden in websites and also other unauthorized coin mining applications.
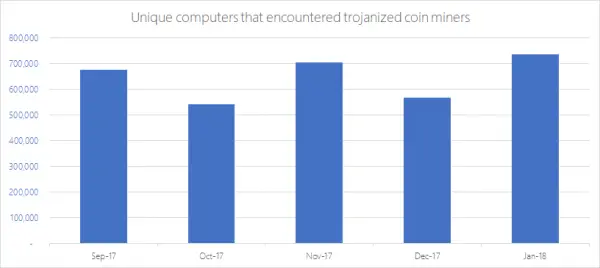
A quick look at the graph above will tell us about the existential threat from cybercriminals when it comes to Trojanized Coin miners. According to the statistics, every month from September 2017 to January 2018, an average of 644,000 unique computers have had an encounter with coin mining malware. Interestingly, the increase in cryptocurrency miners coincides with the corresponding decrease in the Ransomware attack instances. Here is a billion dollar question, are cybercriminals shifting to cryptocurrency mining as the primary source of income?
Microsoft has apparently seen a wide range of malicious cryptocurrency miners and some of them do employ a sophisticated mechanism. It is also worth mentioning that the use of exploits or self-distributing malware is also pretty rampant.
The importance of Persistence
Another interesting trend is the persistence. Microsoft’s research mentions that persistence is essential when it comes to cryptocurrency miners. Apart from common methods like scheduled tasks and autostart registry entries, the cybercriminals may also make use of other advanced methods like code injection and fileless techniques.
Spreading dynamics
Similar to other malware, some of the coin miners also come with spreading capabilities. For instance, a miner that is detected as Worm:Win32/NeksMiner.A drops the payload in the root folder of all the available drives and also spreads to external drives. Other cryptomining scams include browser-based coin miners a.k.a cryptojacking and the infamous tech support scams.
You can read more here on Microsoft.com.
Leave a Reply