In an enterprise environment, efficient discovery and remediation of security issues are of paramount importance. Folks at Microsoft Defender Advanced Threat Protection (ATP) have announced the public preview of a new risk news feed feature called Event Timeline. This new threat timeline feature essentially allows IT admins to discover the origin of a particular security threat. Additionally, they can also determine their future of course of action to eliminate the risk of a particular security threat spreading within the organization.
Microsoft Defender adds Event Timeline
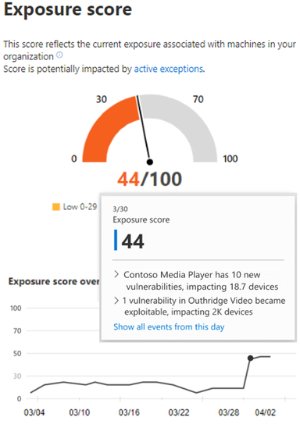
Thanks to the addition of Event Timeline, Microsoft Defender ATP’s threat and vulnerability management capabilities are expected to get even stronger. This security news feed feature will further help security and IT teams “reduce organizational exposure” and “increase organizational resilience,” Microsoft has stated. In its recent blog post, the company talked about the significance of the exposure score in the organization:
“One of the key metrics admins track is the exposure score in their organization – it helps them understand how exposed their organization is to threats as a result of vulnerabilities on devices they manage. The lower the score, the less risk exists.
Microsoft Defender ATP’s Event Timeline will provide organizations with a glimpse of their exposure score. This way, they can easily determine the cause of large changes. Organizations can reduce their exposure score by addressing remediating risks depending on the “prioritized security recommendations.”
Thanks to Event Timeline, organizations can track major security events that affect them the most.
“You can find new vulnerabilities that were introduced, vulnerabilities that became exploitable, exploit that was added to an exploit kit, and more.”
What are these ‘Exposure scores’ all about?
In a common enterprise scenario, IT admins and security teams can view the Exposure score and top events that may have happened over the weekend. The scores vary depending on the impact and severity of particular risks on machines. However, decision-making is extremely crucial since organizations often fail to prioritize their response to those risks. This is where the Event Timeline is likely to come in handy.
IT and security teams can view a list of events in chronological order by the date, related component, the number of originally impacted machines, among other things.
Leave a Reply