Microsoft has achieved a considerable level of progress in avoiding the exploitation of its native kernel components. However, the problem continues to loom large as attackers have started targeting third-party kernel drivers. This new domain has thus become an important area of research for security analysts. It is important for computer manufacturers to secure their tools and software components like drivers as a kernel. Why? Even one flawed component could jeopardize the functionality and make the whole kernel security design fall into ruins. Unfortunately, Microsoft discovered this vulnerability in a driver while investigating an alert raised by Microsoft Defender Advanced Threat Protection’s kernel sensors.
Privilege escalation flaw discovered by Microsoft Defender ATP
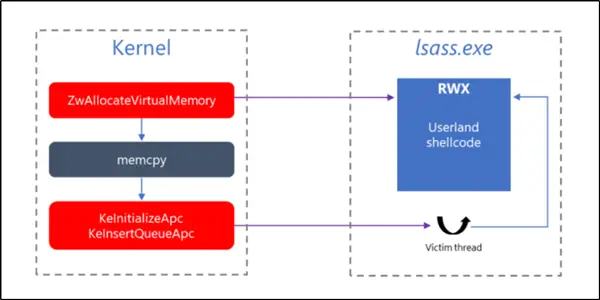
Starting in Windows 10, version 1809, the kernel has been instrumented with new sensors designed to trace User APC code injection initiated by a kernel code, providing better visibility into kernel threats like DOUBLEPULSAR.
We discovered such a driver while investigating an alert raised by Microsoft Defender Advanced Threat Protection’s kernel sensors. We traced the anomalous behavior to a device management driver developed by Huawei. Digging deeper, we found a lapse in the design that led to a vulnerability that could allow local privilege escalation, mentioned a blog post.
Microsoft Defender ATP uses these sensors to detect suspicious operations invoked by a kernel code that might lead to code injection into user-mode. This feature has been the strength of Microsoft Defender ATP’s sensors. Its sensors are designed to expose anomalous behavior and give SecOps personnel the intelligence and tools to investigate threats.
The vulnerabilities overlooked by the component manufacturers should have been kept in mind as it is mandatory that software and products are designed with utmost security in mind. Attack surface should be minimized as much as possible.
Microsoft also disclosed that the flaws, in this case, could have been prevented had the necessary precautions been taken and followed. To prevent more of such instances, the company provides its driver security checklist.
You can read it on the Hardware Dev Center web page. The list gives some guidelines for driver developers to help reduce the risk of drivers being compromised.
For more information on the topic, see Microsoft Security blog post.
Leave a Reply