Microsoft Defender Advanced Threat Protection (ATP) now provides Windows 10 users with a new Unified Extensible Firmware Interface (UEFI) scanner to prevent hardware and firmware-level attacks. What is the UEFI scanner, you ask? Well, it is the newly-added component to Microsoft Defender Antivirus, which is an integral part of Microsoft Defender ATP. UEFI scanner is capable of scanning inside of the firmware filesystem and performing security assessments.
Microsoft Defender ATP gets new UEFI scanner
In its recent blog post, Microsoft Defender ATP Team wrote:
“Hardware and firmware-level attacks have continued to rise in recent years, as modern security solutions made persistence and detection evasion on the operating system more difficult. Attackers compromise the boot flow to achieve low-level malware behavior that’s hard to detect, posing a significant risk to an organization’s security posture.”
Microsoft Defender ATP is an endpoint security platform for Windows 10 users to help them secure their remote machine, identify vulnerabilities, among other things. In addition to its existing protection capabilities, Microsoft Defender ATP now wants to help Windows 10 users safeguard their computer system against various firmware attacks, courtesy of the UEFI scanner.
Before we talk about its actual working, let us first look at the basic concept of the UEFI scanner in Microsoft Defender ATP for Windows 10. There is no denying the fact that hardware and firmware-level attacks continue to increase. At the same time, modern security solutions have become more advanced, preventing persistency and detection evasion of attacks on the operating system to a significant extent.
“Attackers compromise the boot flow to achieve low-level malware behavior that’s hard to detect, posing a significant risk to an organization’s security posture.”
Windows Defender System Guard currently provides Windows 10 users with certain secure boot features to mitigate the risks and challenges posed by firmware attacks. Aiming to make firmware scanning broadly available on Windows 10. The UEFI scanner component expands on Microsoft Defender ATP’s existing secure boot features.
The UEFI scanner is a new component of the built-in antivirus solution on Windows 10 and gives Microsoft Defender ATP the unique ability to scan inside of the firmware filesystem and perform security assessment.
How the new UEFI scanner works
Microsoft is also working with chipset manufacturers to integrate their insights into Microsoft Defender ATP’s UEFI scanner.
The UEFI scanner interacts with the motherboard chipset and scans through the firmware filesystem at runtime. It performs a security assessment with the help of several new solutions, as follows:
- UEFI anti-rootkit
- Full filesystem scanner
- Detection engine
The three-step procedure of the UEFI scanner requires reaching firmware, analyzing content inside the firmware, and identifying malicious behaviors, which is reported in Windows Security, under Protection history.
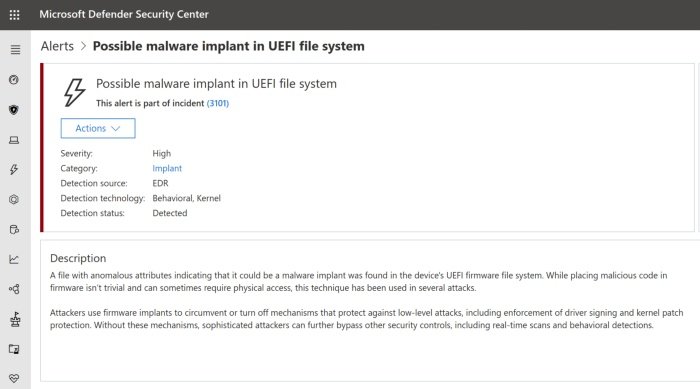
In addition to Windows Security, Microsoft Defender ATP also issues alerts in Microsoft Defender Security Center. This way, security researchers and experts can probe into imminent firmware-level threats.
Additionally, Microsoft Defender ATP’s advanced hunting capabilities also make firmware threat detection possible.
In order to detect unknown threats in Serial Peripheral Interface (SPI) flash, insights gathered from the UEFI scanner are further examined to discover anomalies that are reported to the Microsoft Defender Security Center for investigation.
Why we require the new UEFI scanner
The UEFI replaces legacy BIOS. In the case of hardware-based attacks, attackers deploy rootkit on a vulnerable firmware or a misconfigured machine. It allows attackers to take control of the machine to perform malicious activities. To ensure firmware security, it is essential that the chipset is configured correctly and secure boot is enabled.
To tamper with the firmware security, attackers can also deprivilege the operating system kernel or antivirus.
“If secure boot is disabled or if the motherboard chipset is misconfigured, attackers can change the contents of UEFI drivers that are unsigned or tampered with in the firmware.”
The firmware code is stored in the Serial Peripheral Interface (SPI) flash, and this code is briefly run during UEFI’s SEC phase when a computer runs. Attackers can tamper with the BIOS control register on poorly-configured devices. This way, attackers evade detection by making it difficult to examine what is being executed during the boot. This is what the new UEFI scanner is trying to fix.
Since firmware is stored in SPI flash storage, Microsoft Defender ATP’s new UEFI scanner must follow hardware protocol designed by OEMs.
In related news, Microsoft Defender ATP has taken the wraps off its newly redesigned alerts page as a public preview in the Microsoft Defender Security Center.
Meanwhile, check if your PC supports UEFI or BIOS.