The Hafnium vulnerability has been threatening thousands of Microsoft Exchange and Calendar servers for the past few weeks. It was expected that the exposure could lead to the compromise of systems in around 30,000 US organizations. A few days after releasing a major patch to the issue, Microsoft has released a one-click mitigation tool targeted at small companies that use Microsoft services.
Automatically mitigate CVE-2021-26855 on any Exchange server
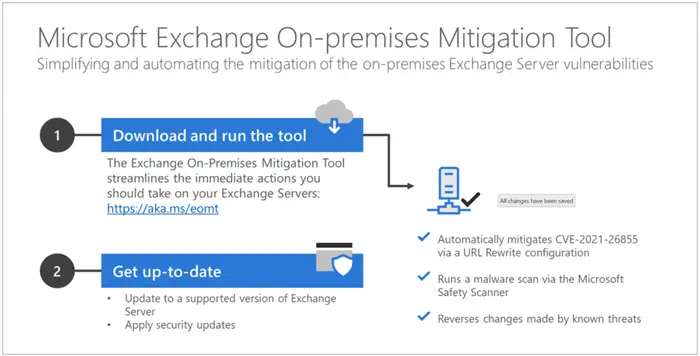
Compared to the central patch, this one-click tool is easy to use and does not require a fully-fledged IT department. Microsoft says that this tool should be used as temporary mitigation only and that companies will have to make changes to servers as per the central patch.
Microsoft aims to say that the one-click patch is not a long-term solution to the Hafnium vulnerability. It has been designed to protect an Exchange server from threats that Microsoft has identified so far. It means the patch will not help customers prevent future attacks from the same hacker group or other.
“We have been actively working with customers through our customer support teams, third-party hosters, and partner network to help them secure their environments and respond to associated threats from the recent Exchange Server on-premises attacks. Based on these engagements we realized that there was a need for a simple, easy to use, automated solution that would meet the needs of customers using both current and out-of-support versions of on-premises Exchange Server,” Microsoft said.
However, when considered a temporary mitigation solution, the one-click patch is a solace to many companies. They can download and run the application to use a few methods to mitigate the issues. For instance, the one-click patch will use Microsoft Safety Scanner to identify the potential threats from the category and reverse the changes. That is, in a few minutes, Microsoft Exchange and Calendar servers will be back to normalcy.
Considering that the Hafnium vulnerability continues to spread fear across the industry, this one-click patch will help thousands of small companies that cannot afford a dedicated IT department. It is also worth noting that the hacker group has exploited various organizations, including hospitals, nonprofits, credit unions, and local governments across the globe.
Primary research indicates that hundreds of thousands of servers have come under the attack. While customers can use one of the company patches, Microsoft will continue looking at how the Chinese hacking group managed to infiltrate such an insane number of devices.
Some experts at the company have noted that the attackers have gathered the sensitive information required for the hack through Microsoft’s security partners.
Leave a Reply