Microsoft and Intel are together studying novel applications of Deep Learning, which is a Machine Learning technique, for malware classification. As part of this collaboration, researchers from Microsoft Threat Protection Intelligence Team and Intel Labs are exploring new malware detection techniques.
Researchers study new malware classification methods
Malware classification determines the threat level, which is an understandably vital and important process in mitigating the challenges, in addition to circumventing the risks of data theft, bypassing access controls, among other things.
In its recent blog post, Microsoft wrote:
“The use of deep learning methods for detecting threats drives a lot of innovation across Microsoft. The collaboration with Intel Labs researchers is just one of the ways in which Microsoft researchers and data scientists continue to explore novel ways to improve security overall.”
Researchers from Microsoft and Intel are exploring the unchartered territory of deep learning applications for malware classification, especially those leveraging computer vision to static malware classification as well as hardware capabilities that improve the performance of deep-learning malware detection approaches.
Well, the static malware classification method involves the analysis of any given malware sample without actually running or executing the code.
Security researchers combined Intel’s prior work on deep transfer learning for static malware classification and Microsoft’s real-world dataset. Together, both companies were looking to determine the practicality of leveraging computer vision to static malware classification.
“It (static analysis) is especially useful for pre-execution detection engines: static analysis disassembles code without having to run applications or monitor runtime behavior.”
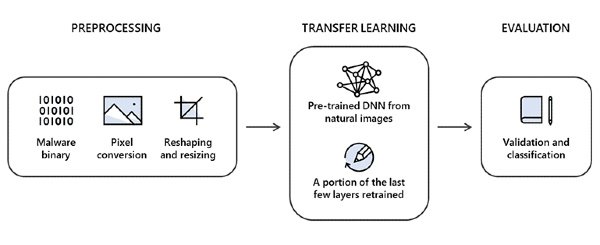
Microsoft and Intel security researchers used an approach called STAMINA. Short for the static malware-as-image network analysis, the STAMINA approach promises the utmost accuracy in detecting malware with “low false positives.”
The STAMINA approach performs a static analysis of malware codes represented as images. This approach consists of three important steps, as follows:
- Image conversion
- Transfer learning
- Evaluation
As per the study, the STAMINA approach achieves a recall of 87.05% at 0.1% false-positive rate, in addition to 99.66% recall and 99.07% accuracy at 2.58% false-positive rate overall.
“The results certainly encourage the use of deep transfer learning for the purpose of malware classification.”
The STAMINA approach may not be effective for bigger size applications since converting billions of pixels into JPEG images and then resizing them is not feasible. For bigger size applications, the metadata-based approach may be effective.
In case you are looking for more technical details of this combined study, download this white paper from the official Intel website.
Leave a Reply